Page 28 - Digital Financial Services security assurance framework
P. 28
8�1 Threat: Account and Session Hijacking
The general threat here is the ability of an attacker to take control of an account or communication session. The
vulnerabilities are manifested in different ways at the DFS provider and the MNO.
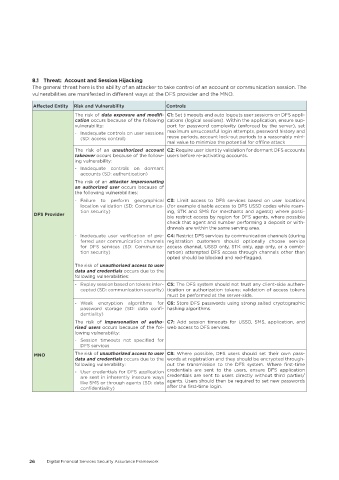
Affected Entity Risk and Vulnerability Controls
The risk of data exposure and modifi- C1: Set timeouts and auto logouts user sessions on DFS appli-
cation occurs because of the following cations (logical sessions). Within the application, ensure sup-
vulnerability: port for password complexity (enforced by the server), set
- Inadequate controls on user sessions maximum unsuccessful login attempts, password history and
(SD: access control) reuse periods, account lock-out periods to a reasonably mini-
mal value to minimize the potential for offline attack
The risk of an unauthorized account C2: Require user identity validation for dormant DFS accounts
takeover occurs because of the follow- users before re-activating accounts.
ing vulnerability:
- Inadequate controls on dormant
accounts (SD: authentication)
The risk of an attacker impersonating
an authorized user occurs because of
the following vulnerabilities:
- Failure to perform geographical C3: Limit access to DFS services based on user locations
location validation (SD: Communica- (for example disable access to DFS USSD codes while roam-
tion security) ing, STK and SMS for merchants and agents) where possi-
DFS Provider ble restrict access by region for DFS agents, where possible
check that agent and number performing a deposit or with-
drawals are within the same serving area.
- Inadequate user verification of pre- C4: Restrict DFS services by communication channels (during
ferred user communication channels registration customers should optionally choose service
for DFS services (SD: Communica- access channel, USSD only, STK only, app only, or a combi-
tion security) nation) attempted DFS access through channels other than
opted should be blocked and red-flagged.
The risk of unauthorised access to user
data and credentials occurs due to the
following vulnerabilities:
- Replay session based on tokens inter- C5: The DFS system should not trust any client-side authen-
cepted (SD: communication security) tication or authorization tokens; validation of access tokens
must be performed at the server-side.
- Weak encryption algorithms for C6: Store DFS passwords using strong salted cryptographic
password storage (SD: data confi- hashing algorithms.
dentiality)
The risk of impersonation of autho- C7: Add session timeouts for USSD, SMS, application, and
rised users occurs because of the fol- web access to DFS services.
lowing vulnerability:
- Session timeouts not specified for
DFS services
MNO The risk of unauthorized access to user C8: Where possible, DFS users should set their own pass-
data and credentials occurs due to the words at registration and they should be encrypted through-
following vulnerability: out the transmission to the DFS system. Where first-time
- User credentials for DFS application credentials are sent to the users, ensure DFS application
are sent in inherently insecure ways credentials are sent to users directly without third parties/
like SMS or through agents (SD: data agents. Users should then be required to set new passwords
confidentiality) after the first-time login.
26 Digital Financial Services Security Assurance Framework