Page 1007 - Cloud computing: From paradigm to operation
P. 1007
Security 7
9.7 Security threats and challenges in monitoring data destruction stage
a) spoofing: Attackers could masquerade as the management system of the cloud monitoring service
and cause the loss of other monitoring data.
b) operating system vulnerability: Monitoring data could be lost during data usage due to a system
vulnerability.
9.8 Security threats and challenges in monitoring data backup stage
a) operating system vulnerability: Monitoring data could be lost during the data backup and result in
the inability to restore data due to a system vulnerability.
10 Security requirements for monitoring data of cloud computing
This clause identifies the data security requirements for the monitoring service of cloud computing.
10.1 Security requirements for monitoring data collection
The data security requirements for the monitoring data collection include the following:
a) optional monitoring data is required to be created only by CSC request;
b) it is recommended to provide notification to the CSC when necessary monitoring data is created;
c) it is recommended to notify the CSC of the scope of monitoring data;
d) it is required to maintain integrity and accuracy of monitoring data;
e) it is recommended to use standard data acquisition techniques;
f) it is recommended to provide access control methods to the interfaces of monitoring data
acquisition such as white list, black list, etc.;
g) it is recommended to provide cryptographic methods to ensure the security of the monitoring data
acquisition interface;
h) it is recommended to use standard network protocols between the cloud resources and monitoring
data storage servers.
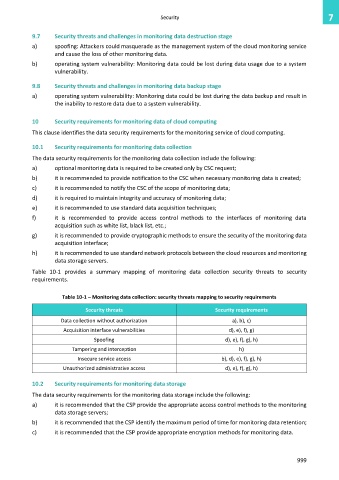
Table 10-1 provides a summary mapping of monitoring data collection security threats to security
requirements.
Table 10-1 – Monitoring data collection: security threats mapping to security requirements
Security threats Security requirements
Data collection without authorization a), b), c)
Acquisition interface vulnerabilities d), e), f), g)
Spoofing d), e), f), g), h)
Tampering and interception h)
Insecure service access b), d), e), f), g), h)
Unauthorized administrative access d), e), f), g), h)
10.2 Security requirements for monitoring data storage
The data security requirements for the monitoring data storage include the following:
a) it is recommended that the CSP provide the appropriate access control methods to the monitoring
data storage servers;
b) it is recommended that the CSP identify the maximum period of time for monitoring data retention;
c) it is recommended that the CSP provide appropriate encryption methods for monitoring data.
999