Page 1009 - Cloud computing: From paradigm to operation
P. 1009
Security 7
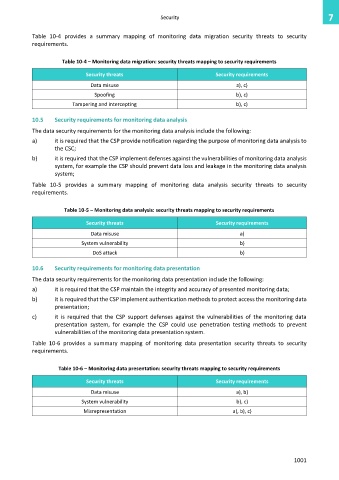
Table 10-4 provides a summary mapping of monitoring data migration security threats to security
requirements.
Table 10-4 – Monitoring data migration: security threats mapping to security requirements
Security threats Security requirements
Data misuse a), c)
Spoofing b), c)
Tampering and intercepting b), c)
10.5 Security requirements for monitoring data analysis
The data security requirements for the monitoring data analysis include the following:
a) it is required that the CSP provide notification regarding the purpose of monitoring data analysis to
the CSC;
b) it is required that the CSP implement defenses against the vulnerabilities of monitoring data analysis
system, for example the CSP should prevent data loss and leakage in the monitoring data analysis
system;
Table 10-5 provides a summary mapping of monitoring data analysis security threats to security
requirements.
Table 10-5 – Monitoring data analysis: security threats mapping to security requirements
Security threats Security requirements
Data misuse a)
System vulnerability b)
DoS attack b)
10.6 Security requirements for monitoring data presentation
The data security requirements for the monitoring data presentation include the following:
a) it is required that the CSP maintain the integrity and accuracy of presented monitoring data;
b) it is required that the CSP implement authentication methods to protect access the monitoring data
presentation;
c) it is required that the CSP support defenses against the vulnerabilities of the monitoring data
presentation system, for example the CSP could use penetration testing methods to prevent
vulnerabilities of the monitoring data presentation system.
Table 10-6 provides a summary mapping of monitoring data presentation security threats to security
requirements.
Table 10-6 – Monitoring data presentation: security threats mapping to security requirements
Security threats Security requirements
Data misuse a), b)
System vulnerability b), c)
Misrepresentation a), b), c)
1001