Page 166 - Big data - Concept and application for telecommunications
P. 166
4 Big data - Concept and application for telecommunications
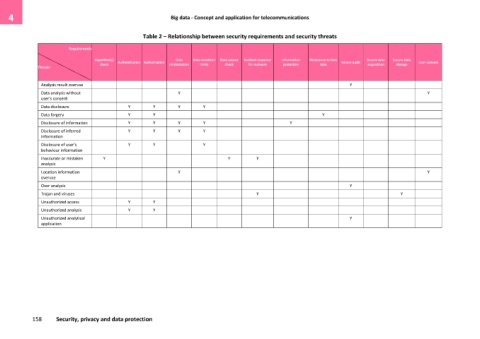
Table 2 – Relationship between security requirements and security threats
Requirements
Algorithm(s) Authentication Authorization Data Data retention Data source Incident response Information Resistance to fake Secure audit Secure data Secure data User consent
check minimization limits check for malware protection data acquisition storage
Threats
Analysis result overuse Y
Data analysis without Y Y
user's consent
Data disclosure Y Y Y Y
Data forgery Y Y Y
Disclosure of information Y Y Y Y Y
Disclosure of inferred Y Y Y Y
information
Disclosure of user's Y Y Y
behaviour information
Inaccurate or mistaken Y Y Y
analysis
Location information Y Y
overuse
Over analysis Y
Trojan and viruses Y Y
Unauthorized access Y Y
Unauthorized analysis Y Y
Unauthorized analytical Y
application
158 Security, privacy and data protection