Page 163 - Big data - Concept and application for telecommunications
P. 163
Big data - Concept and application for telecommunications 4
7.10 Over analysis
Over analysis may occur when the data analysis entity that analyses the big data sets gets more information
than the intended original data analysis.
7.11 Trojan and viruses
These occur when a malicious mobile Internet user or attacker impersonates a legal user and injects Trojans
or viruses into the data which will be collected by a mobile Internet service provider.
7.12 Unauthorized access
This threat occurs when an illegal entity (e.g., a data pre-processing entity, a data analysis entity) gains big
data analyst results or even original data by masquerading as an authorized entity.
7.13 Unauthorized analysis
Unauthorized analysis occurs when an un-authorized entity analyses the big data from mobile Internet
services by masquerading as an authorized entity.
7.14 Unauthorized analytical application
This may occur when tampered data analysis entity/data application entity or the attackers impersonate a
legal entity to use the analytical result to develop business insights and mechanisms including prediction and
decision assistance.
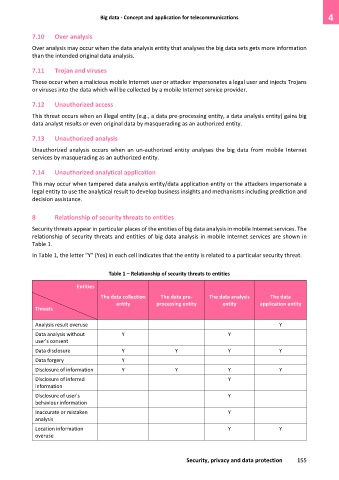
8 Relationship of security threats to entities
Security threats appear in particular places of the entities of big data analysis in mobile Internet services. The
relationship of security threats and entities of big data analysis in mobile Internet services are shown in
Table 1.
In Table 1, the letter "Y" (Yes) in each cell indicates that the entity is related to a particular security threat.
Table 1 – Relationship of security threats to entities
Entities
The data collection The data pre- The data analysis The data
entity processing entity entity application entity
Threats
Analysis result overuse Y
Data analysis without Y Y
user's consent
Data disclosure Y Y Y Y
Data forgery Y
Disclosure of information Y Y Y Y
Disclosure of inferred Y
information
Disclosure of user's Y
behaviour information
Inaccurate or mistaken Y
analysis
Location information Y Y
overuse
Security, privacy and data protection 155