Page 170 - Big data - Concept and application for telecommunications
P. 170
4 Big data - Concept and application for telecommunications
– long term, where it would take a relatively longer time to recover the system, for example, one
month.
The security recovery function could be used for recovery of the mobile Internet service provider's assets
such as system, software, hardware etc., when they are attacked by an attacker or malicious user.
11.9 User reminder
User reminder provides a mechanism to guarantee that the data collected from the mobile Internet service
usage will be used in the big data analysis has been authorized by the mobile Internet services user.
The key point is that for a certain mobile Internet service that needs to collect user data, the service is to
send a reminder to the user, to display it, and to briefly explain it to the user.
The user can be reminded whether data collection is planned and what data will be collected. They will also
be informed how the data will be processed and handled.
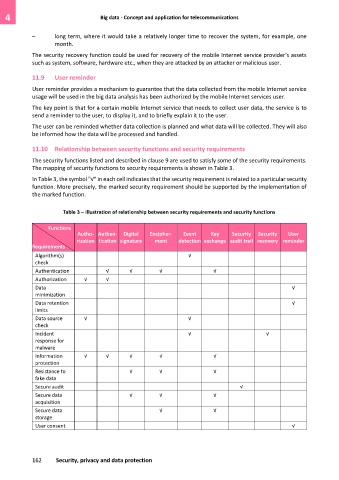
11.10 Relationship between security functions and security requirements
The security functions listed and described in clause 9 are used to satisfy some of the security requirements.
The mapping of security functions to security requirements is shown in Table 3.
In Table 3, the symbol "√" in each cell indicates that the security requirement is related to a particular security
function. More precisely, the marked security requirement should be supported by the implementation of
the marked function.
Table 3 – Illustration of relationship between security requirements and security functions
Functions
Autho- Authen- Digital Encipher- Event Key Security Security User
rization tication signature ment detection exchange audit trail recovery reminder
Requirements
Algorithm(s) √
check
Authentication √ √ √ √
Authorization √ √
Data √
minimization
Data retention √
limits
Data source √ √
check
Incident √ √
response for
malware
Information √ √ √ √ √
protection
Resistance to √ √ √
fake data
Secure audit √
Secure data √ √ √
acquisition
Secure data √ √
storage
User consent √
162 Security, privacy and data protection