Page 212 - Trust in ICT 2017
P. 212
3 Trust in ICT
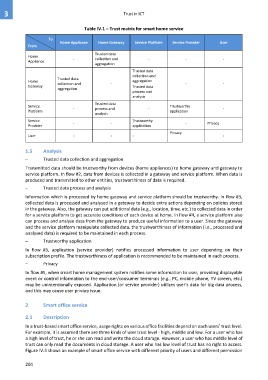
Table IV.1 – Trust matrix for smart home service
To
Home Appliance Home Gateway Service Platform Service Provider User
From
Trusted data
Home - collection and - - -
Appliance
aggregation
Trusted data
collection and
Trusted data
Home collection and - aggregation - -
Gateway Trusted data
aggregation
process and
analysis
Trusted data
Service Trustworthy
Platform - process and - application -
analysis
Service Trustworthy
Provider - - application - Privacy
Privacy
User - - - -
1.5 Analysis
– Trusted data collection and aggregation
Transmitted data should be trustworthy from devices (home appliances) to home gateway and gateway to
service platform. In flow #2, data from devices is collected in a gateway and service platform. When data is
produced and transmitted to other entities, trustworthiness of data is required.
– Trusted data process and analysis
Information which is processed by home gateway and service platform should be trustworthy. In flow #3,
collected data is processed and analysed in a gateway to decide extra actions depending on policies stored
in the gateway. Also, the gateway can put additional data (e.g., location, time, etc.) to collected data in order
for a service platform to get accurate conditions of each device at home. In flow #4, a service platform also
can process and analyse data from the gateway to produce useful information to a user. Since the gateway
and the service platform manipulate collected data, the trustworthiness of information (i.e., processed and
analysed data) is required to be maintained in each process.
– Trustworthy application
In flow #5, application (service provider) notifies processed information to user depending on their
subscription profile. The trustworthiness of application is recommended to be maintained in each process.
– Privacy
In flow #5, when smart home management system notifies some information to user, providing displayable
event or control information to the end-user/consumer terminals (e.g., PC, mobile phone, TV screen, etc.)
may be unintentionally exposed. Application (or service provider) utilizes user’s data for big data process,
and this may cause user privacy issue.
2 Smart office service
2.1 Description
In a trust-based smart office service, usage rights on various office facilities depend on each users’ trust level.
For example, it is assumed there are three kinds of user trust level - high, middle and low. For a user who has
a high level of trust, he or she can read and write the cloud storage. However, a user who has middle level of
trust can only read the documents in cloud storage. A user who has low level of trust has no right to access.
Figure IV.3 shows an example of smart office service with different priority of users and different permission
204