Page 208 - Trust in ICT 2017
P. 208
3 Trust in ICT
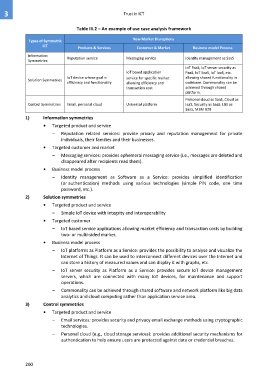
Table III.2 – An example of use case analysis framework
New Market Disruptions
Types of Symmetric
ICT
Products & Services Customer & Market Business model Process
Information
Symmetries Reputation service Messaging service Identity management as SaaS
IoT PaaS, IoT server security as
IoT based application PaaS, IoT SaaS, IoT IaaS, etc.
IoT device whose goal is service for specific market allowing shared functionality in
Solution Symmetries
efficiency and functionality allowing efficiency and codebase. Commonality can be
transaction cost achieved through shared
platform.
Personal cloud as SaaS, Cloud as
Control Symmetries Email, personal cloud Universal platform IaaS, Security as SaaS, LBS as
SaaS, M2M B2B
1) Information symmetries
• Targeted product and service
– Reputation related services: provide privacy and reputation management for private
individuals, their families and their businesses.
• Targeted customer and market
– Messaging services: provides ephemeral messaging service (i.e., messages are deleted and
disappeared after recipients read them).
• Business model process
– Identity management as Software as a Service: provides simplified identification
(or authentication) methods using various technologies (simple PIN code, one time
password, etc.).
2) Solution symmetries
• Targeted product and service
– Simple IoT device with integrity and interoperability
• Targeted customer
– IoT based service applications allowing market efficiency and transaction costs by building
two- or multi-sided market.
• Business model process
– IoT platforms as Platform as a Service: provides the possibility to analyse and visualize the
Internet of Things. It can be used to interconnect different devices over the Internet and
can store a history of measured values and can display it with graphs, etc.
– IoT server security as Platform as a Service: provides secure IoT device management
servers, which are connected with many IoT devices, for maintenance and support
operations.
– Commonality can be achieved through shared software and network platform like big data
analytics and cloud computing rather than application service area.
3) Control symmetries
• Targeted product and service
– Email services: provides security and privacy email exchange methods using cryptographic
technologies.
– Personal cloud (e.g., cloud storage services): provides additional security mechanisms for
authentication to help ensure users are protected against data or credential breaches.
200