Page 161 - Proceedings of the 2017 ITU Kaleidoscope
P. 161
Challenges for a data-driven society
6. ACKNOWLEDGMENT
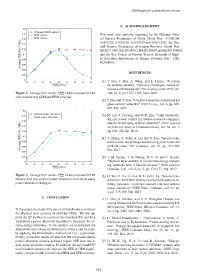
0.2
Proposed SEEM scheme
0.18
SRM scheme This work was partially supported by the National Natu-
EEM scheme
0.16 ral Science Foundation of China (Grant Nos. 61302104,
SEE(bit/J/Hz) 0.14 ural Science Foundation of Jiangsu Province (Grant Nos.
61401223, 61522109, 61631020 and 61671253), the Nat-
0.12
BK20171446, BK 20160911, BK20140887 and BK20150040),
and the Key Project of Natural Science Research of High-
0.1
Average 0.08 er Education Institutions of Jiangsu Province (No. 15K-
JA510003)
0.06
0.04
REFERENCES
0.02
0
20 25 30 35 40 45 50 55 60 [1] Y. Zou, J. Zhu, X. Wang, and L. Hanzo, “A survey
max
P CBS (dbm) on wireless security: Technical challenges, recent ad-
vances and future trends,” Proceedings of the IEEE, vol.
Figure 2. Average SEE versus P max of the proposed SEEM 104, no. 9, pp. 1727-1765, Sept. 2016.
CBS
and conventional SRM and EEM schemes.
[2] J. Zhu and Y. Zou, “Cognitive network cooperation for
green cellular networks,” IEEE Access., vol. 4, pp. 849-
857, Feb. 2016.
0.2
Optimal power allocation
0.18 [3] M. Lin, J. Ouyang, and W.-P. Zhu, “Joint beamform-
Equal power allocation
ing and power control for device-to-device communi-
0.16 cations underlaying cellular networks,” IEEE Journal
SEE(bit/J/Hz) 0.14 [4] Y. Zhang, Z. Yang, A. Liu and Y. Zou, “Secure trans-
on Selected Areas in Communications, vol. 34, no. 1,
pp. 138-150, Jan. 2016.
0.12
0.1
Average 0.08 mission over the wiretap channel using polar codes and
artificial noise,” IET Commun., vol. 11, pp. 377-384,
0.06
0.04 Feb. 2017.
0.02 [5] T. M. Hoang, T. Q. Duong, N.-S. Vo and C. Kundu,
“Physical layer security in cooperative energy harvest-
0
20 25 30 35 40 45 50 55 60 ing networks with a friendly jammer,” IEEE wireless
P max (dbm)
CBS
Commun. Lett., vol. 6, no. 2, pp. 174-177, Apr. 2017.
Figure 3. Average SEE versus P max of the proposed SEEM
CBS [6] H. Wu, X. Tao, Z. Han, N. Li and J. Xu, “Secure trans-
scheme with the optimal power allocation and simple equal mission in MISOME wiretap channel with multiple as-
power allocation strategies. sisting jammers: maximum secrecy rate and optimal
power allocation,” IEEE Trans. Commun., vol. 65, no.
2, pp. 775-789, Feb. 2017.
5. CONCLUSION
[7] J. Zhu, R. Schober, and V. K. Bhargava, “Linear pre-
coding of data and artificial noise in secure massive MI-
MO systems,” IEEE Trans. Wireless Commun., vol. 15,
In this paper, we studied the use of artificial noise to improve
no. 3, pp. 2245-2261, Mar. 2016.
the physical-layer security of underlay CRNs. We first ap-
plied the ZF method to construct the downlink BF, and then [8] H. Shokri-Ghadikolaei, I. Glaropoulos, V. Fodor, C.
formulated a power allocation algorithm to maximize the se- Fischione and A. Ephremides, “Green sensing and ac-
crecy energy efficiency. To be specific, we transformed the cess: Energy-throughput trade-offs in cognitive net-
formulated non-convex problem into a convex one by joint- working,” IEEE Commun. Mag., vol. 53, no. 11, pp.
ly applying the Dinkelbach’s method and D.C. approaches. 199-207, Nov. 2015.
Finally, numerical results showed that the proposed optimal
power allocation scheme achieves higher SEE than the e- [9] D. W. K. Ng, E. S. Lo and R. Schober, “Energy-
qual power allocation scheme. In addition, the proposed SEE Efficient resource allocation in OFDMA systems with
maximization scheme can improve the SEE of CRN signifi- large numbers of base station antennas,” IEEE Com-
cantly compared with conventional SRM and EEM schemes. mun. Trans., vol. 11, no. 9, pp. 3292-3304, Sep. 2012.
– 145 –