Page 82 - ITU-T Focus Group Digital Financial Services – Technology, innovation and competition
P. 82
ITU-T Focus Group Digital Financial Services
Technology, Innovation and Competition
1 Scope
This report describes the vendor platform features expected of a typical digital financial service (DFS)
deployment, which includes access options, cooperation with third party partners, mobile money operator
(MMO), MMO interoperability, service function, and system features, in order to present the recommendation
and suggestions for the study phase.
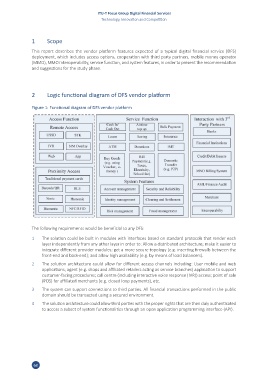
2 Logic functional diagram of DFS vendor platform
Figure 1: Functional diagram of DFS vendor platform
The following requirements would be beneficial to any DFS:
1 The solution could be built in modules with interfaces based on standard protocols that render each
layer independently from any other layer in order to: Allow a distributed architecture; make it easier to
integrate different provider modules; get a more secure topology (e.g. inserting firewalls between the
front-end and back-end); and allow high availability (e.g. by means of load balancers).
2 The solution architecture could allow for different access channels including: User mobile and web
applications; agent (e.g. shops and affiliated retailers acting as service branches) application to support
customer-facing procedures; call centre (including interactive voice response (IVR)) access; point of sale
(POS) for affiliated merchants (e.g. closed loop payments), etc.
3 The system can support connections to third parties. All financial transactions performed in the public
domain should be transacted using a secured environment.
4 The solution architecture could allow third parties with the proper rights that are then duly authenticated
to access a subset of system functionalities through an open application programming interface (API).
68