Page 16 - ITU-T Focus Group Digital Financial Services – Technology, innovation and competition
P. 16
ITU-T Focus Group Digital Financial Services
Technology, Innovation and Competition
1 Introduction
Digital financial services (DFS) offer tremendous promise to enable financial inclusion, the delivery of financial
services at low cost to low-income and otherwise disadvantaged segments of society. Mobile money and
payment systems, also known as branchless banking systems, have had particular impact on consumers.
Generally deployed by companies outside of the traditional financial services sector (e.g., telecommunications
providers), branchless banking systems rely on the common deployment of cellular networks and mobile
devices around the world. Over the past decade, these systems have revolutionized the way in which money
is used in developing economies.
Because citizens no longer need to carry large amounts of currency or travel long distances to make payments,
DFS systems have been largely viewed as an improvement to physical security. However, there are many other
emerging security threats within the DFS ecosystem from cyber-enabled attackers to the expansion of the
stakeholders into numerous and sometimes competing parties. This document provides an overview of security
challenges and threats that face the DFS environment. Multiple stakeholders need to be involved in order to
secure the DFS environment. This requires that security be managed at multiple layers, from operational policy
to securing associated hardware and software.
2 Recommendation ITU-T X.805 Security Management Standard
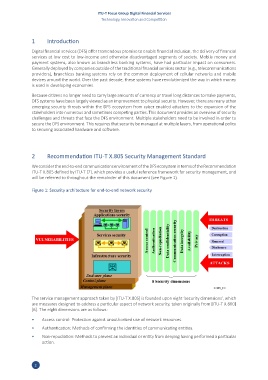
We consider the end-to-end communications environment of the DFS ecosystem in terms of the Recommendation
ITU-T X.805 defined by ITU-T [7], which provides a useful reference framework for security management, and
will be referred to throughout the remainder of this document (see Figure 1).
Figure 1: Security architecture for end-to-end network security
The service management approach taken by [ITU-T X.805] is founded upon eight ‘security dimensions’, which
are measures designed to address a particular aspect of network security, taken originally from [ITU-T X.800]
[6]. The eight dimensions are as follows:
• Access control: Protection against unauthorised use of network resources.
• Authentication: Methods of confirming the identities of communicating entities.
• Non-repudiation: Methods to prevent an individual or entity from denying having performed a particular
action.
2