Page 20 - ITU-T Focus Group Digital Financial Services – Technology, innovation and competition
P. 20
ITU-T Focus Group Digital Financial Services
Technology, Innovation and Competition
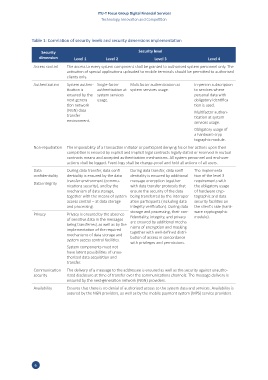
Table 1: Correlation of security levels and security dimensions implementation
Security Security level
dimension Level 1 Level 2 Level 3 Level 4
Access control The access to every system component shall be granted to authorised system personnel only. The
activation of special applications uploaded to mobile terminals should be permitted to authorised
clients only.
Authentication System authen- Single-factor Multifactor authentication at In-person subscription
tication is authentication at system services usage. to services where
ensured by the system services personal data with
next-genera- usage. obligatory identifica-
tion network tion is used.
(NGN) data Multifactor authen-
transfer tication at system
environment. services usage.
Obligatory usage of
a hardware cryp-
tographic module.
Non-repudiation The impossibility of a transaction initiator or participant denying his or her actions upon their
completion is ensured by explicit and implicit legal contracts legally stated or reserved in mutual
contracts means and accepted authentication mechanisms. All system personnel and end-user
actions shall be logged. Event logs shall be change-proof and hold all actions of all users.
Data During data transfer, data confi- During data transfer, data confi- The implementa-
confidentiality dentiality is ensured by the data dentiality is ensured by additional tion of the level 3
transfer environment (commu- message encryption together requirements with
Data integrity
nications security), and by the with data transfer protocols that the obligatory usage
mechanism of data storage, ensure the security of the data of hardware cryp-
together with the means of system being transferred by the interoper- tographic and data
access control – at data storage ation participants (including data security facilities on
and processing. integrity verification). During data the client's side (hard-
storage and processing, their con- ware cryptographic
Privacy Privacy is ensured by the absence fidentiality, integrity, and privacy module).
of sensitive data in the messages are ensured by additional mecha-
being transferred, as well as by the
implementation of the required nisms of encryption and masking
together with well-defined distri-
mechanisms of data storage and
system access control facilities. bution of access in concordance
with privileges and permissions.
System components must not
have latent possibilities of unau-
thorized data acquisition and
transfer.
Communication The delivery of a message to the addressee is ensured as well as the security against unautho-
security rized disclosure at time of transfer over the communications channels. The message delivery is
ensured by the next-generation network (NGN) providers.
Availability Ensures that there is no denial of authorized access to the system data and services. Availability is
assured by the NGN providers, as well as by the mobile payment system (MPS) service providers.
6