Page 1043 - Shaping smarter and more sustainable cities - Striving for sustainable development goals
P. 1043
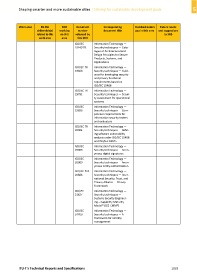
Work area FG‐SSC SDO Document Corresponding Standardization Future needs
deliverable(s) working number document title gap in this area and suggestions
related to this on this released by to SG5
work area area this SDO
ISO/IEC Information Technology —
19249 TR Security techniques — Cata‐
logue of Architectural and
Design Principles for Secure
Products, Systems, and
Applications
ISO/IEC TR Information Technology —
19608 Security techniques — Guid‐
ance for developing security
and privacy functional
requirements based on
ISO/IEC 15408
ISO/IEC TR Information Technology —
19791 Security techniques — Securi‐
ty assessment for operational
systems
ISO/IEC Information Technology —
19896 Security techniques — Com‐
petence requirements for
information security testers
and evaluators
ISO/IEC TR Information Technology —
20004 Security techniques — Refin‐
ing software vulnerability
analysis under ISO/IEC 15408
and ISO/IEC 18045
ISO/IEC Information Technology —
20008 Security techniques — Anon‐
ymous digital signatures
ISO/IEC Information Technology —
20009 Security techniques — Anon‐
ymous entity authentication
ISO/IEC PAS Information Technology —
20886 Security techniques — Inter‐
national Security, Trust, and
Privacy Alliance — Privacy
Framework
ISO/IEC Information Technology —
21827 Security techniques —
Systems Security Engineer‐
ing – Capability Maturity
Model® (SSE‐CMM®)
ISO/IEC Information Technology —
24760 Security techniques — A
framework for identity
management
ITU‐T's Technical Reports and Specifications 1033