Page 1042 - Shaping smarter and more sustainable cities - Striving for sustainable development goals
P. 1042
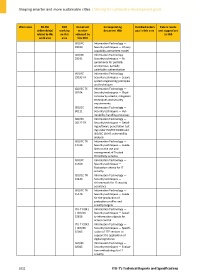
Work area FG‐SSC SDO Document Corresponding Standardization Future needs
deliverable(s) working number document title gap in this area and suggestions
related to this on this released by to SG5
work area area this SDO
ISO/IEC Information Technology —
29190 Security techniques — Privacy
capability assessment model
ISO/IEC Information Technology —
29191 Security techniques — Re‐
quirements for partially
anonymous, partially
unlinkable authentication
ISO/IEC Information Technology —
29193 TR Security techniques — Secure
system engineering principles
and techniques
ISO/IEC TS Information Technology —
30104 Security techniques — Physi‐
cal security attacks, mitigation
techniques and security
requirements
ISO/IEC Information Technology —
30111 Security techniques — Vul‐
nerability handling processes
ISO/IEC Information Technology —
30127 TR Security techniques — Detail‐
ing software penetration test‐
ing under ISO/IEC 15408 and
ISO/IEC 18045 vulnerability
analysis
ISO/IEC TR Information Technology —
14516 Security techniques — Guide‐
lines on the use and
management of Trusted
Third Party services
ISO/IEC Information Technology —
15408 Security techniques —
Evaluation criteria for IT
security
ISO/IEC TR Information Technology —
15443 Security techniques —
A framework for IT security
assurance
ISO/IEC TR Information Technology —
15446 Security techniques — Guide
for the production of
protection profiles and
security targets
ITU‐T X.841 Information Technology —
| ISO/IEC Security techniques — Securi‐
15816 ty information objects for
access control
ITU‐T X.843 Information Technology —
| ISO/IEC Security techniques — Specifi‐
15945 cation of TTP services to
support the application of
digital signatures
ISO/IEC Information Technology —
18045 Security techniques — Evalua‐
tion methodology for IT
security
1032 ITU‐T's Technical Reports and Specifications