Page 560 - Unleashing the potenti al of the Internet of Things
P. 560
5 Unleashing the potential of the Internet of Things
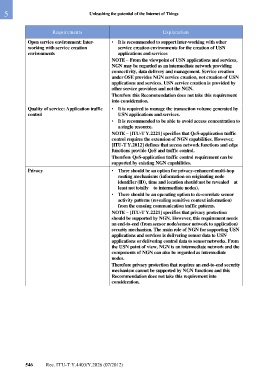
Requirements Explanation
Open service environment: Inter- • It is recommended to support inter-working with other
working with service creation service creation environments for the creation of USN
environments applications and services
NOTE – From the viewpoint of USN applications and services,
NGN may be regarded as an intermediate network providing
connectivity, data delivery and management. Service creation
under OSE provides NGN service creation, not creation of USN
applications and services. USN service creation is provided by
other service providers and not the NGN.
Therefore this Recommendation does not take this requirement
into consideration.
Quality of service: Application traffic • It is required to manage the transaction volume generated by
control USN applications and services.
• It is recommended to be able to avoid access concentration to
a single resource.
NOTE – [ITU-T Y.2221] specifies that QoS-application traffic
control requires the extension of NGN capabilities. However,
[ITU-T Y.2012] defines that access network functions and edge
functions provide QoS and traffic control.
Therefore QoS-application traffic control requirement can be
supported by existing NGN capabilities.
Privacy • There should be an option for privacy-enhanced multi-hop
routing mechanisms (information on originating node
identifier (ID), time and location should not be revealed – at
least not totally – to intermediate nodes).
• There should be an operating option to de-correlate sensor
activity patterns (revealing sensitive context information)
from the ensuing communication traffic patterns.
NOTE – [ITU-T Y.2221] specifies that privacy protection
should be supported by NGN. However, this requirement needs
an end-to-end (from sensor node/sensor network to application)
security mechanism. The main role of NGN for supporting USN
applications and services is delivering sensor data to USN
applications or delivering control data to sensor networks. From
the USN point of view, NGN is an intermediate network and the
components of NGN can also be regarded as intermediate
nodes.
Therefore privacy protection that requires an end-to-end security
mechanism cannot be supported by NGN functions and this
Recommendation does not take this requirement into
consideration.
546 Rec. ITU-T Y.4403/Y.2026 (07/2012)