Page 545 - Cloud computing: From paradigm to operation
P. 545
Cloud Computing management 2
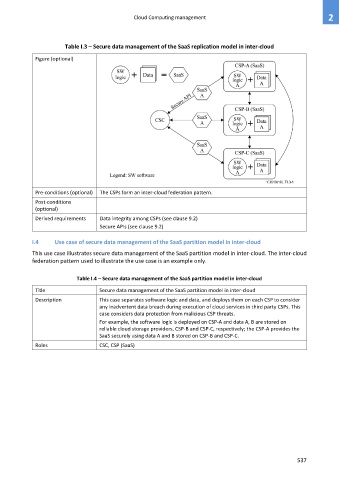
Table I.3 – Secure data management of the SaaS replication model in inter-cloud
Figure (optional)
Pre-conditions (optional) The CSPs form an inter-cloud federation pattern.
Post-conditions
(optional)
Derived requirements Data integrity among CSPs (see clause 9.2)
Secure APIs (see clause 9.2)
I.4 Use case of secure data management of the SaaS partition model in inter-cloud
This use case illustrates secure data management of the SaaS partition model in inter-cloud. The inter-cloud
federation pattern used to illustrate the use case is an example only.
Table I.4 – Secure data management of the SaaS partition model in inter-cloud
Title Secure data management of the SaaS partition model in inter-cloud
Description This case separates software logic and data, and deploys them on each CSP to consider
any inadvertent data breach during execution of cloud services in third party CSPs. This
case considers data protection from malicious CSP threats.
For example, the software logic is deployed on CSP-A and data A, B are stored on
reliable cloud storage providers, CSP-B and CSP-C, respectively; the CSP-A provides the
SaaS securely using data A and B stored on CSP-B and CSP-C.
Roles CSC, CSP (SaaS)
537