Page 67 - ITU Journal Future and evolving technologies Volume 2 (2021), Issue 5 – Internet of Everything
P. 67
ITU Journal on Future and Evolving Technologies, Volume 2 (2021), Issue 5
authors of [17] explores using LN for delivering patch While LN is mostly serving end users and merchants,
updates to the IoT devices. They employ LN in the there are other entities within it that serve different pur‑
process of claiming rewards upon successful delivery of poses. For example, an end user trying to connect to the
the patch updates. LN using a mobile device will be connecting to a gateway
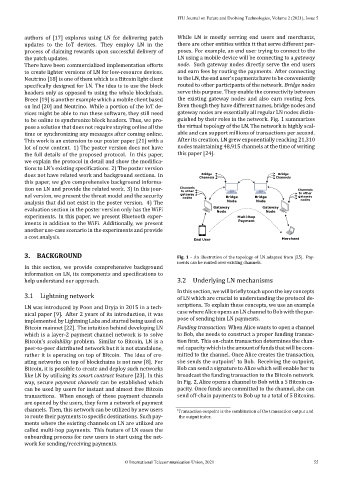
There have been commercialized implementation efforts node. Such gateway nodes directly serve the end users
to create lighter versions of LN for low‑resource devices. and earn fees by routing the payments. After connecting
Neutrino [18] is one of them which is a Bitcoin light client to the LN, the end user’s payments have to be conveniently
speci ically designed for LN. The idea is to use the block routed to other participants of the network. Bridge nodes
headers only as opposed to using the whole blockchain. serve this purpose. They enable the connectivity between
Breez [19] is another example which a mobile client based the existing gateway nodes and also earn routing fees.
on lnd [20] and Neutrino. While a portion of the IoT de‑ Even though they have different names, bridge nodes and
vices might be able to run these software, they still need gateway nodes are essentially all regular LN nodes distin‑
to be online to synchronize block headers. Thus, we pro‑ guished by their roles in the network. Fig. 1 summarizes
pose a solution that does not require staying online all the the virtual topology of the LN. The network is highly scal‑
time or synchronizing any messages after coming online. able and can support millions of transactions per second.
This work is an extension to our poster paper [21] with a After its creation, LN grew exponentially reaching 21,310
lot of new content. 1) The poster version does not have nodes maintaining 48,915 channels at the time of writing
this paper [24].
the full details of the proposed protocol. In this paper,
we explain the protocol in detail and show the modi ica‑
tions to LN’s existing speci ications. 2) The poster version
Bridge Bridge
does not have related work and background sections. In
Channels Channels
this paper, we give comprehensive background informa‑
Channels
tion on LN and provide the related work. 3) In this jour‑ Channels
to other
gateway to other
nal version, we present the threat model and the security nodes Bridge Bridge gateway
Node Node nodes
analysis that did not exist in the poster version. 4) The
Gateway Gateway
evaluation section in the poster version only has the WiFi Node Node
experiments. In this paper, we present Bluetooth exper‑ Multi-hop
Payment
iments in addition to the WiFi. Additionally, we present
another use‑case scenario in the experiments and provide
a cost analysis. End User Merchant
3. BACKGROUND Fig. 1 – An illustration of the topology of LN adapted from [25]. Pay‑
ments can be routed over existing channels.
In this section, we provide comprehensive background
information on LN, its components and speci ications to
help understand our approach. 3.2 Underlying LN mechanisms
In this section, we will brie ly touch upon the key concepts
3.1 Lightning network of LN which are crucial to understanding the protocol de‑
scriptions. To explain these concepts, we use an example
LN was introduced by Poon and Dryja in 2015 in a tech‑
case where Alice opens an LN channel to Bob with the pur‑
nical paper [9]. After 2 years of its introduction, it was
pose of sending him LN payments.
implemented by Lightning Labs and started being used on
Bitcoin mainnet [22]. The intuition behind developing LN Funding transaction: When Alice wants to open a channel
which is a layer‑2 payment channel network is to solve to Bob, she needs to construct a proper funding transac‑
Bitcoin’s scalability problem. Similar to Bitcoin, LN is a tion irst. This on‑chain transaction determines the chan‑
peer‑to‑peer distributed network but it is not standalone, nel capacity which is the amount of funds that will be com‑
rather it is operating on top of Bitcoin. The idea of cre‑ mitted to the channel. Once Alice creates the transaction,
1
ating networks on top of blockchains is not new [8]. For she sends the outpoint to Bob. Receiving the outpoint,
Bitcoin, it is possible to create and deploy such networks Bob can send a signature to Alice which will enable her to
like LN by utilizing its smart contract feature [23]. In this broadcast the funding transaction to the Bitcoin network.
way, secure payment channels can be established which In Fig. 2, Alice opens a channel to Bob with a 5 Bitcoin ca‑
can be used by users for instant and almost free Bitcoin pacity. Once funds are committed to the channel, she can
transactions. When enough of these payment channels send off‑chain payments to Bob up to a total of 5 Bitcoins.
are opened by the users, they form a network of payment
channels. Then, this network can be utilized by new users
1
Transaction outpoint is the combination of the transaction output and
to route their payments to speci ic destinations. Such pay‑ the output index.
ments where the existing channels on LN are utilized are
called multi‑hop payments. This feature of LN eases the
onboarding process for new users to start using the net-
work for sending/receiving payments.
© International Telecommunication Union, 2021 55