Page 17 - FIGI: Security audit of various DFS applications
P. 17
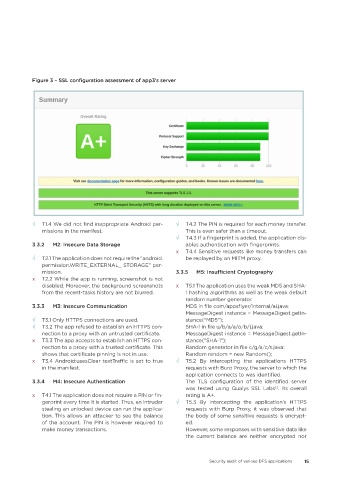
Figure 3 – SSL configuration assessment of app3’s server
√ T1.4 We did not find inappropriate Android per- √ T4.2 The PIN is required for each money transfer.
missions in the manifest. This is even safer than a timeout.
√ T4.3 If a fingerprint is added, the application dis-
3.3.2 M2: Insecure Data Storage ables authentication with fingerprints.
x T4.4 Sensitive requests like money transfers can
√ T2.1 The application does not require the "android. be replayed by an MITM proxy.
permission.WRITE_EXTERNAL_ STORAGE" per-
mission. 3.3.5 M5: Insufficient Cryptography
x T2.2 While the app is running, screenshot is not
disabled. Moreover, the background screenshots x T5.1 The application uses the weak MD5 and SHA-
from the recent-tasks history are not blurred. 1 hashing algorithms as well as the weak default
random number generator.
3.3.3 M3: Insecure Communication MD5 in file com/appsflyer/internal/ai.java:
MessageDigest instance = MessageDigest.getIn-
√ T3.1 Only HTTPS connections are used. stance("MD5");
√ T3.2 The app refused to establish an HTTPS con- SHA-1 in file u/b/a/a/o/b/j.java:
nection to a proxy with an untrusted certificate. MessageDigest instance = MessageDigest.getIn-
x T3.3 The app accepts to establish an HTTPS con- stance("SHA-1");
nection to a proxy with a trusted certificate. This Random generator in file c/g/a/c/s.java:
shows that certificate pinning is not in use. Random random = new Random();
x T3.4 Android: usesClear textTraffic is set to true √ T5.2 By intercepting the applications HTTPS
in the manifest. requests with Burp Proxy, the server to which the
application connects to was identified.
3.3.4 M4: Insecure Authentication The TLS configuration of the identified server
was tested using Qualys SSL Labs . Its overall
12
x T4.1 The application does not require a PIN or fin- rating is A+.
gerprint every time it is started. Thus, an intruder √ T5.3 By intercepting the application’s HTTPS
stealing an unlocked device can run the applica- requests with Burp Proxy, it was observed that
tion. This allows an attacker to see the balance the body of some sensitive requests is encrypt-
of the account. The PIN is however required to ed.
make money transactions. However, some responses with sensitive data like
the current balance are neither encrypted nor
Security audit of various DFS applications 15