Page 16 - FIGI: Security audit of various DFS applications
P. 16
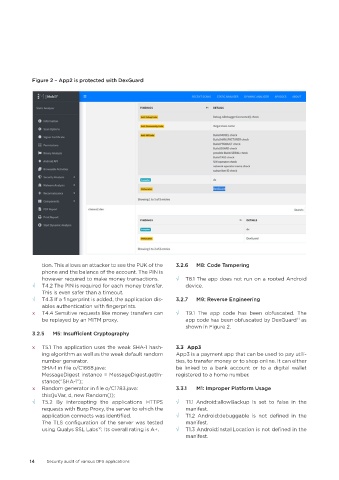
Figure 2 – App2 is protected with DexGuard
tion. This allows an attacker to see the PUK of the 3.2.6 M8: Code Tampering
phone and the balance of the account. The PIN is
however required to make money transactions. √ T8.1 The app does not run on a rooted Android
√ T4.2 The PIN is required for each money transfer. device.
This is even safer than a timeout.
√ T4.3 If a fingerprint is added, the application dis- 3.2.7 M9: Reverse Engineering
ables authentication with fingerprints.
x T4.4 Sensitive requests like money transfers can √ T9.1 The app code has been obfuscated. The
be replayed by an MITM proxy. app code has been obfuscated by DexGuard as
11
shown in Figure 2.
3.2.5 M5: Insufficient Cryptography
x T5.1 The application uses the weak SHA-1 hash- 3�3 App3
ing algorithm as well as the weak default random App3 is a payment app that can be used to pay utili-
number generator. ties, to transfer money or to shop online. It can either
SHA-1 in file o/C1668.java: be linked to a bank account or to a digital wallet
MessageDigest instance = MessageDigest.getIn- registered to a home number.
stance("SHA-1");
x Random generator in file o/C1783.java: 3.3.1 M1: Improper Platform Usage
this(juVar, d, new Random());
√ T5.2 By intercepting the applications HTTPS √ T1.1 Android: allowBackup is set to false in the
requests with Burp Proxy, the server to which the manifest.
application connects was identified. √ T1.2 Android: debuggable is not defined in the
The TLS configuration of the server was tested manifest.
using Qualys SSL Labs . Its overall rating is A+. √ T1.3 Android: installLocation is not defined in the
10
manifest.
14 Security audit of various DFS applications