Page 12 - FIGI: Security analysis of the KaiOS feature phone platform for DFS applications Security, Infrastructure and Trust Working Group
P. 12
4 KNOWN SECURITY ISSUES IN KAIOS
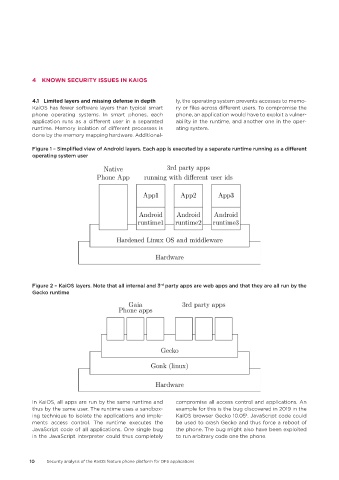
4�1 Limited layers and missing defense in depth ly, the operating system prevents accesses to memo-
KaiOS has fewer software layers than typical smart ry or files across different users. To compromise the
phone operating systems. In smart phones, each phone, an application would have to exploit a vulner-
application runs as a different user in a separated ability in the runtime, and another one in the oper-
runtime. Memory isolation of different processes is ating system.
done by the memory mapping hardware. Additional-
Figure 1 – Simplified view of Android layers. Each app is executed by a separate runtime running as a different
operating system user
Figure 2 – KaiOS layers. Note that all internal and 3 party apps are web apps and that they are all run by the
rd
Gecko runtime
In KaiOS, all apps are run by the same runtime and compromise all access control and applications. An
thus by the same user. The runtime uses a sandbox- example for this is the bug discovered in 2019 in the
ing technique to isolate the applications and imple- KaiOS browser Gecko 10.05 . JavaScript code could
4
ments access control. The runtime executes the be used to crash Gecko and thus force a reboot of
JavaScript code of all applications. One single bug the phone. The bug might also have been exploited
in the JavaScript interpreter could thus completely to run arbitrary code one the phone.
10 Security analysis of the KaiOS feature phone platform for DFS applications