Page 21 - Digital Financial Services security assurance framework
P. 21
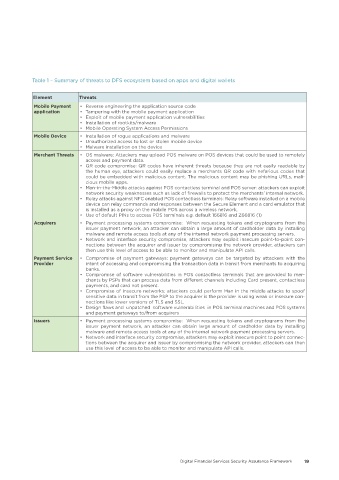
Table 1 – Summary of threats to DFS ecosystem based on apps and digital wallets
Element Threats
Mobile Payment • Reverse engineering the application source code
application • Tampering with the mobile payment application
• Exploit of mobile payment application vulnerabilities
• Installation of rootkits/malware
• Mobile Operating System Access Permissions
Mobile Device • Installation of rogue applications and malware
• Unauthorized access to lost or stolen mobile device
• Malware installation on the device
Merchant Threats • OS malware: Attackers may upload POS malware on POS devices that could be used to remotely
access and payment data.
• QR code compromise: QR codes have inherent threats because they are not easily readable by
the human eye, attackers could easily replace a merchants QR code with nefarious codes that
could be embedded with malicious content. The malicious content may be phishing URLs, mali-
cious mobile apps.
• Man-in-the-Middle attacks against POS contactless terminal and POS server: attackers can exploit
network security weaknesses such as lack of firewalls to protect the merchants’ internal network.
• Relay attacks against NFC enabled POS contactless terminals: Relay software installed on a mobile
device can relay commands and responses between the Secure Element and a card emulator that
is installed as a proxy on the mobile POS across a wireless network.
• Use of default PINs to access POS terminals e.g. default 166816 and Z66816 (1)
Acquirers • Payment processing systems compromise: When requesting tokens and cryptograms from the
issuer payment network, an attacker can obtain a large amount of cardholder data by installing
malware and remote access tools at any of the internal network payment processing servers.
• Network and interface security compromise, attackers may exploit insecure point-to-point con-
nections between the acquirer and issuer by compromising the network provider, attackers can
then use this level of access to be able to monitor and manipulate API calls.
Payment Service • Compromise of payment gateways: payment gateways can be targeted by attackers with the
Provider intent of accessing and compromising the transaction data in transit from merchants to acquiring
banks.
• Compromise of software vulnerabilities in POS contactless terminals that are provided to mer-
chants by PSPs that can process data from different channels including Card present, contactless
payments, and card not present.
• Compromise of insecure networks; attackers could perform Man in the middle attacks to spoof
sensitive data in transit from the PSP to the acquirer is the provider is using weak or insecure con-
nections like lower versions of TLS and SSL.
• Design flaws and unpatched software vulnerabilities in POS terminal machines and POS systems
and payment gateways to/from acquirers
Issuers • Payment processing systems compromise: When requesting tokens and cryptograms from the
issuer payment network, an attacker can obtain large amount of cardholder data by installing
malware and remote access tools at any of the internal network payment processing servers.
• Network and interface security compromise, attackers may exploit insecure point to point connec-
tions between the acquirer and issuer by compromising the network provider, attackers can then
use this level of access to be able to monitor and manipulate API calls.
Digital Financial Services Security Assurance Framework 19