Page 992 - Cloud computing: From paradigm to operation
P. 992
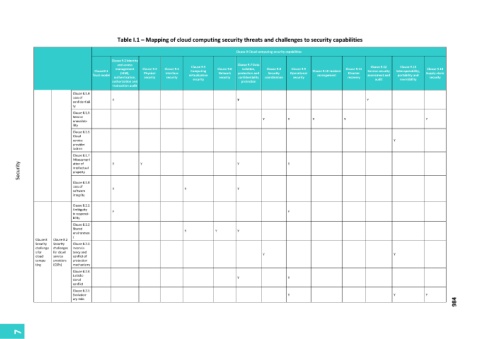
Table I.1 – Mapping of cloud computing security threats and challenges to security capabilities
Clause 9 Cloud computing security capabilities
Clause 9.2 Identity
and access Clause 9.7 Data
management Clause 9.3 Clause 9.4 Clause 9.5 Clause 9.6 isolation, Clause 9.8 Clause 9.9 Clause 9.11 Clause 9.12 Clause 9.13 Clause 9.14
Clause9.1 Computing Clause 9.10 Incident Service security Interoperability,
Trust model (IAM), Physical Interface virtualization Network protection and Security Operational management Disaster assessment and portability and Supply chain
authentication, security security security confidentiality coordination security recovery security
authorization and security protection audit reversibility
transaction audit
Clause 8.1.4
Loss of
confidentiali Y Y Y
ty
Clause 8.1.5
Service Y Y Y Y Y
unavailab-
ility
Clause 8.1.6
Cloud
service Y
provider
lock-in
Clause 8.1.7
Misappropri Y Y Y Y
Security intellectual
ation of
property
Clause 8.1.8
Loss of Y Y Y
software
integrity
Clause 8.2.1
Ambiguity Y Y
in responsi-
bility
Clause 8.2.2
Shared Y Y Y
environmen
t
Clause 8 Clause 8.2
Security Security Clause 8.2.3
challenge challenges Inconsis-
s for for cloud tency and Y Y
cloud service conflict of
compu- providers protection
ting (CSPs) mechanisms
Clause 8.2.4
Jurisdic- Y Y
tional
conflict
Clause 8.2.5
Evolution- Y Y Y
984
ary risks
7