Page 990 - Cloud computing: From paradigm to operation
P. 990
7 Security
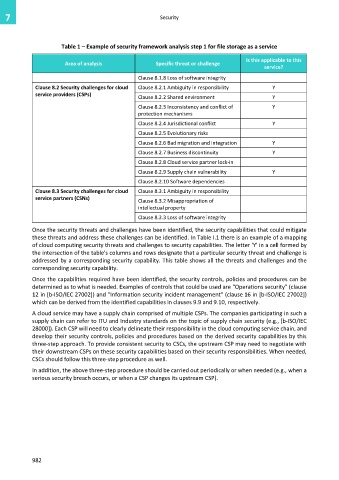
Table 1 – Example of security framework analysis step 1 for file storage as a service
Is this applicable to this
Area of analysis Specific threat or challenge
service?
Clause 8.1.8 Loss of software integrity
Clause 8.2 Security challenges for cloud Clause 8.2.1 Ambiguity in responsibility Y
service providers (CSPs)
Clause 8.2.2 Shared environment Y
Clause 8.2.3 Inconsistency and conflict of Y
protection mechanisms
Clause 8.2.4 Jurisdictional conflict Y
Clause 8.2.5 Evolutionary risks
Clause 8.2.6 Bad migration and integration Y
Clause 8.2.7 Business discontinuity Y
Clause 8.2.8 Cloud service partner lock-in
Clause 8.2.9 Supply chain vulnerability Y
Clause 8.2.10 Software dependencies
Clause 8.3 Security challenges for cloud Clause 8.3.1 Ambiguity in responsibility
service partners (CSNs)
Clause 8.3.2 Misappropriation of
intellectual property
Clause 8.3.3 Loss of software integrity
Once the security threats and challenges have been identified, the security capabilities that could mitigate
these threats and address these challenges can be identified. In Table I.1 there is an example of a mapping
of cloud computing security threats and challenges to security capabilities. The letter 'Y' in a cell formed by
the intersection of the table's columns and rows designate that a particular security threat and challenge is
addressed by a corresponding security capability. This table shows all the threats and challenges and the
corresponding security capability.
Once the capabilities required have been identified, the security controls, policies and procedures can be
determined as to what is needed. Examples of controls that could be used are "Operations security" (clause
12 in [b-ISO/IEC 27002]) and "Information security incident management" (clause 16 in [b-ISO/IEC 27002])
which can be derived from the identified capabilities in clauses 9.9 and 9.10, respectively.
A cloud service may have a supply chain comprised of multiple CSPs. The companies participating in such a
supply chain can refer to ITU and Industry standards on the topic of supply chain security (e.g., [b-ISO/IEC
28000]). Each CSP will need to clearly delineate their responsibility in the cloud computing service chain, and
develop their security controls, policies and procedures based on the derived security capabilities by this
three-step approach. To provide consistent security to CSCs, the upstream CSP may need to negotiate with
their downstream CSPs on these security capabilities based on their security responsibilities. When needed,
CSCs should follow this three-step procedure as well.
In addition, the above three-step procedure should be carried out periodically or when needed (e.g., when a
serious security breach occurs, or when a CSP changes its upstream CSP).
982