Page 745 - Cloud computing: From paradigm to operation
P. 745
XaaS 3
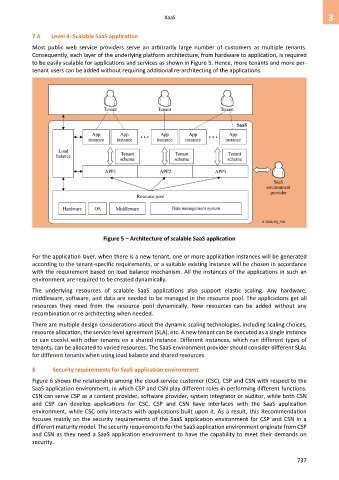
7.4 Level 4: Scalable SaaS application
Most public web service providers serve an arbitrarily large number of customers as multiple tenants.
Consequently, each layer of the underlying platform architecture, from hardware to application, is required
to be easily scalable for applications and services as shown in Figure 5. Hence, more tenants and more per-
tenant users can be added without requiring additional re-architecting of the applications.
Figure 5 – Architecture of scalable SaaS application
For the application layer, when there is a new tenant, one or more application instances will be generated
according to the tenant-specific requirements, or a suitable existing instance will be chosen in accordance
with the requirement based on load balance mechanism. All the instances of the applications in such an
environment are required to be created dynamically.
The underlying resources of scalable SaaS applications also support elastic scaling. Any hardware,
middleware, software, and data are needed to be managed in the resource pool. The applications get all
resources they need from the resource pool dynamically. New resources can be added without any
recombination or re-architecting when needed.
There are multiple design considerations about the dynamic scaling technologies, including scaling choices,
resource allocation, the service level agreement (SLA), etc. A new tenant can be executed as a single instance
or can coexist with other tenants on a shared instance. Different instances, which run different types of
tenants, can be allocated to varied resources. The SaaS environment provider should consider different SLAs
for different tenants when using load balance and shared resources.
8 Security requirements for SaaS application environment
Figure 6 shows the relationship among the cloud service customer (CSC), CSP and CSN with respect to the
SaaS application environment, in which CSP and CSN play different roles in performing different functions.
CSN can serve CSP as a content provider, software provider, system integrator or auditor, while both CSN
and CSP can develop applications for CSC. CSP and CSN have interfaces with the SaaS application
environment, while CSC only interacts with applications built upon it. As a result, this Recommendation
focuses mainly on the security requirements of the SaaS application environment for CSP and CSN in a
different maturity model. The security requirements for the SaaS application environment originate from CSP
and CSN as they need a SaaS application environment to have the capability to meet their demands on
security.
737