Page 1066 - Cloud computing: From paradigm to operation
P. 1066
7 Security
9.3 User responsibilities
The objective specified in clause 9.3 of ISO/IEC 27002 applies.
9.3.1 Use of secret authentication information
Control 9.3.1 and the associated implementation guidance and other information specified in ISO/IEC 27002
apply.
9.4 System and application access control
The objective specified in clause 9.4 of ISO/IEC 27002 applies.
9.4.1 Information access restriction
Control 9.4.1 and the associated implementation guidance and other information specified in ISO/IEC 27002
apply. The following sector-specific guidance also applies.
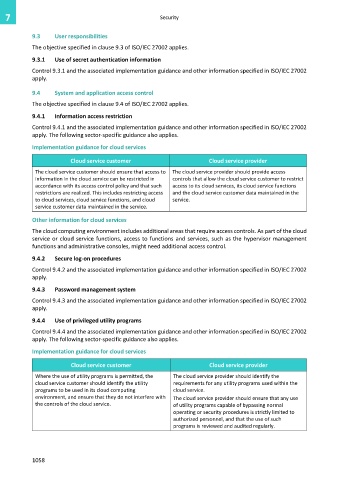
Implementation guidance for cloud services
Cloud service customer Cloud service provider
The cloud service customer should ensure that access to The cloud service provider should provide access
information in the cloud service can be restricted in controls that allow the cloud service customer to restrict
accordance with its access control policy and that such access to its cloud services, its cloud service functions
restrictions are realized. This includes restricting access and the cloud service customer data maintained in the
to cloud services, cloud service functions, and cloud service.
service customer data maintained in the service.
Other information for cloud services
The cloud computing environment includes additional areas that require access controls. As part of the cloud
service or cloud service functions, access to functions and services, such as the hypervisor management
functions and administrative consoles, might need additional access control.
9.4.2 Secure log-on procedures
Control 9.4.2 and the associated implementation guidance and other information specified in ISO/IEC 27002
apply.
9.4.3 Password management system
Control 9.4.3 and the associated implementation guidance and other information specified in ISO/IEC 27002
apply.
9.4.4 Use of privileged utility programs
Control 9.4.4 and the associated implementation guidance and other information specified in ISO/IEC 27002
apply. The following sector-specific guidance also applies.
Implementation guidance for cloud services
Cloud service customer Cloud service provider
Where the use of utility programs is permitted, the The cloud service provider should identify the
cloud service customer should identify the utility requirements for any utility programs used within the
programs to be used in its cloud computing cloud service.
environment, and ensure that they do not interfere with The cloud service provider should ensure that any use
the controls of the cloud service. of utility programs capable of bypassing normal
operating or security procedures is strictly limited to
authorized personnel, and that the use of such
programs is reviewed and audited regularly.
1058