Page 170 - ITU KALEIDOSCOPE, ATLANTA 2019
P. 170
2019 ITU Kaleidoscope Academic Conference
4. PRELIMINARY ARCHITECTURE PROPOSAL the functionality (e.g. access control, auditing, context
integrity checks) to use the data to be shared with the health
The architecture proposed in this paper is framed for a very service providers; this is achieved through the cloning and
specific digital health scenario, specific requirements and migration of the DataAgent from the PHIX main container
specific context. The scenario is that of sharing personal to the service provider containers, and provides inter-agent
health information data (e.g. health indicators collected on communication and synchronization between the associated
personal monitoring devices, historical health records and DataAgents. The data owner has control of his community
digital phenotypes [34]) with a health service provider, and of DataAgents with the ability to gain visibility of where his
ensuring legibility, agency and negotiability in the data has been shared, to understand the specific utilization of
interaction between the individual and their data. A subset of their data and to control the use of specific DataAgents, for
the requirements detailed in the previous section can be met example, updating permissions and access control, revoking
and implemented with standard techniques and solutions. and killing shared agents.
For example, some of the requirements around data privacy
can be handled using information security techniques, such
as public cryptography systems [35], as has been the practice
for say HIPAA compliance and, more recently, GDPR
compliance. However, there are specific requirements
associated with the HDI imperatives, specifically
negotiability, that give motivation for the architecture
proposed in this paper. In particular, the architecture
addresses the requirement for enhancing the control that
owners of data retain over their data once the data is shared,
and ensuring that the dynamic contextual constraints are
enforced on the subsequent use of the data.
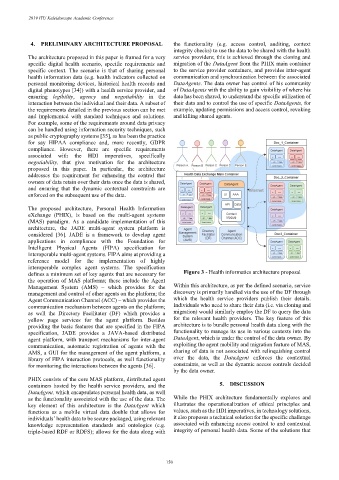
The proposed architecture, Personal Health Information
eXchange (PHIX), is based on the multi-agent systems
(MAS) paradigm. As a candidate implementation of this
architecture, the JADE multi-agent system platform is
considered [36]. JADE is a framework to develop agent
applications in compliance with the Foundation for
Intelligent Physical Agents (FIPA) specification for
interoperable multi-agent systems. FIPA aims at providing a
reference model for the implementation of highly
interoperable complex agent systems. The specification
defines a minimum set of key agents that are necessary for Figure 3 - Health informatics architecture proposal
the operation of MAS platforms; these include the Agent
Management System (AMS) – which provides for the Within this architecture, as per the defined scenario, service
management and control of other agents on the platform; the discovery is primarily handled via the use of the DF through
Agent Communication Channel (ACC) – which provides the which the health service providers publish their details.
communication mechanism between agents on the platform; Individuals who need to share their data (i.e. via cloning and
as well the Directory Facilitator (DF) which provides a migration) would similarly employ the DF to query the data
yellow page services for the agent platform. Besides for the relevant health providers. The key feature of this
providing the basic features that are specified in the FIPA architecture is to bundle personal health data along with the
specification, JADE provides a JAVA-based distributed functionality to manage its use in various contexts into the
agent platform, with transport mechanisms for inter-agent DataAgent, which is under the control of the data owner. By
communication, automatic registration of agents with the exploiting the agent mobility and migration feature of MAS,
AMS, a GUI for the management of the agent platform, a sharing of data is not associated with relinquishing control
library of FIPA interaction protocols, as well functionality over the data, the DataAgent enforces the contextual
for monitoring the interactions between the agents [36]. constraints, as well as the dynamic access controls decided
by the data owner.
PHIX consists of the core MAS platform, distributed agent
containers hosted by the health service providers, and the 5. DISCUSSION
DataAgent, which encapsulates personal health data, as well
as the functionality associated with the use of the data. The While the PHIX architecture fundamentally explores and
key element of this architecture is the DataAgent which illustrates the operationalization of ethical principles and
functions as a mobile virtual data double that allows for values, such as the HDI imperatives, in technology solutions,
individuals’ health data to be secure packaged, using relevant it also proposes a technical solution for the specific challenge
knowledge representation standards and ontologies (e.g. associated with enhancing access control to and contextual
triple-based RDF or RDFS); allows for the data along with integrity of personal health data. Some of the solutions that
– 150 –