Page 169 - ITU KALEIDOSCOPE, ATLANTA 2019
P. 169
ICT for Health: Networks, standards and innovation
is being used; but legibility is also defined with regards to 3.3 Negotiability
the algorithms that process the data, towards ensuring that
algorithms are understood and that the various forms of Negotiability is defined in terms of “active and engaged
algorithm opacity are reasonably mitigated [33]. While at a interaction with data as contexts change.” This makes
simple level the “concerned” people could be understood to recognition of the fact that not only do situations and
refer to the people who the data is about, in reality, the people contexts change, but also do individuals’ desires, attitudes
who are impacted by collected health data, which Loi [34] and preferences. The use of personal health data is tightly
terms as digital phenotypes, and the nature of the impact are coupled to and contingent on the context; individuals need to
very diverse. In the case of health informatics, there are the retain the legibility and agency in different contexts. This
identified individuals who the data is about; there are further decomposes into the following considerations:
individuals who collect the data and who are involved in the
creation and shaping of the digital phenotypes, and there are 1. (Perpetual) Control: the continued ownership and
also people who are impacted by generalizations that control of personal health data and digital phenotypes,
emanate from health informatics [34]. In this paper, the the digital traces that have value towards specific health
notion of “ownership” of data is used in the first sense, which outcomes, in perpetuity [34].
regards health informatics as the self-extension of and as 2. Data provenance: with the changing contexts and the
being constitutive of the individual who the data is about. evolution of data, it is vital to maintain the genealogy of
personal health data.
From the analysis of Mortier et al.’s [31] description and
discussion of “legibility,” supported by the investigations
undertaken in this research, the following health informatics
systems requirements and considerations are formulated:
1. Accounting and auditing: to keep track of and enable an
inspectable audit of the use of personal health data.
Further, to allow for the auditing of the associated
algorithms.
2. Feedback and notifications: to inform the owners of the
collection and use of their data.
3. Relevant insights: to provide actionable insights that
facilitate the subsequent use of the data.
3.2 Agency
Agency is defined in terms of enhancing “the capacity for the
humans to act in these data systems” [31]. Enhancing
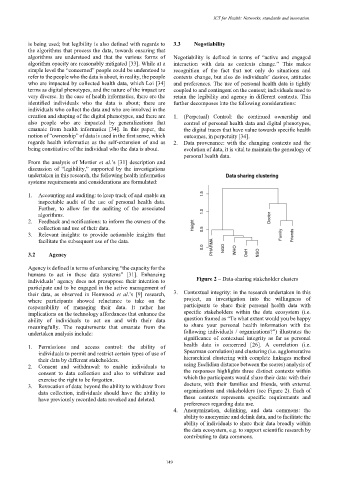
individuals’ agency does not presuppose their intention to Figure 2 – Data-sharing stakeholder clusters
participate and to be engaged in the active management of
their data, as observed in Henwood et al.’s [9] research, 3. Contextual integrity: in the research undertaken in this
where participants showed reluctance to take on the project, an investigation into the willingness of
responsibility of managing their data. It rather has participants to share their personal health data with
implications on the technology affordances that enhance the specific stakeholders within the data ecosystem (i.e.
ability of individuals to act on and with their data question framed as “To what extent would you be happy
meaningfully. The requirements that emanate from the to share your personal health information with the
undertaken analysis include: following individuals / organizations?”) illustrates the
significance of contextual integrity as far as personal
1. Permissions and access control: the ability of health data is concerned [26]. A correlation (i.e.
individuals to permit and restrict certain types of use of Spearman correlation) and clustering (i.e. agglomerative
their data by different stakeholders. hierarchical clustering with complete linkages method
2. Consent and withdrawal: to enable individuals to using Euclidian distance between the scores) analysis of
consent to data collection and also to withdraw and the responses highlights three distinct contexts within
exercise the right to be forgotten. which the participants would share their data: with their
3. Revocation of data: beyond the ability to withdraw from doctors, with their families and friends, with external
data collection, individuals should have the ability to organizations and stakeholders (see Figure 2). Each of
have previously recorded data revoked and deleted. these contexts represents specific requirements and
preferences regarding data use.
4. Anonymization, delinking, and data commons: the
ability to anonymize and delink data, and to facilitate the
ability of individuals to share their data broadly within
the data ecosystem, e.g. to support scientific research by
contributing to data commons.
– 149 –