Page 152 - Big data - Concept and application for telecommunications
P. 152
4 Big data - Concept and application for telecommunications
Appendix I
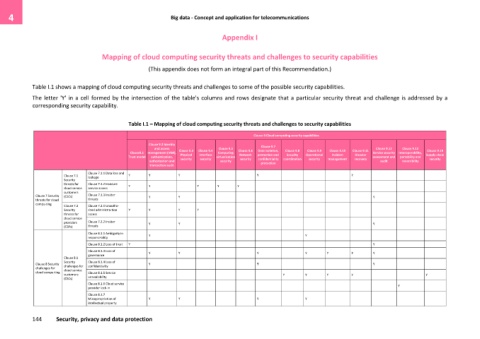
Mapping of cloud computing security threats and challenges to security capabilities
(This appendix does not form an integral part of this Recommendation.)
Table I.1 shows a mapping of cloud computing security threats and challenges to some of the possible security capabilities.
The letter 'Y' in a cell formed by the intersection of the table's columns and rows designate that a particular security threat and challenge is addressed by a
corresponding security capability.
Table I.1 – Mapping of cloud computing security threats and challenges to security capabilities
Clause 9 Cloud computing security capabilities
Clause 9.2 Identity
and access Clause 9.5 Clause 9.7 Clause 9.12 Clause 9.13
Clause 9.3 Clause 9.4 Clause 9.6 Data isolation, Clause 9.8 Clause 9.9 Clause 9.10 Clause 9.11 Clause 9.14
Clause9.1 management (IAM), Computing Service security Interoperability,
Disaster
Incident
Security
Trust model authentication, Physical Interface virtualization Network protection and coordination Operational management recovery assessment and portability and Supply chain
security
security
security
security
authorization and security confidentiality audit reversibility security
protection
transaction audit
Clause 7.1.1 Data loss and
Clause 7.1 leakage Y Y Y Y Y
Security
threats for Clause 7.1.2 Insecure Y Y Y Y Y
cloud service service access
customers
Clause 7 Security (CSCs) Clause 7.1.3 Insider Y Y Y
threats for cloud threats
compu-ting
Clause 7.2 Clause 7.2.1 Unautho-
Security rized administra-tion Y Y Y Y
threats for access
cloud service
providers Clause 7.2.2 Insider Y Y Y
(CSPs) threats
Clause 8.1.1 Ambiguity in Y Y
responsi-bility
Clause 8.1.2 Loss of trust Y Y
Clause 8.1.3 Loss of Y Y Y Y Y Y Y
governance
Clause 8.1
Security Clause 8.1.4 Loss of
Clause 8 Security confidentiality Y Y Y
challenges for challenges for
cloud compu-ting cloud service Clause 8.1.5 Service
customers Y Y Y Y Y
(CSCs) unavailability
Clause 8.1.6 Cloud service Y
provider lock-in
Clause 8.1.7
Misappropriation of Y Y Y Y
intellectual property
144 Security, privacy and data protection