Page 150 - Big data - Concept and application for telecommunications
P. 150
4 Big data - Concept and application for telecommunications
• providing mechanisms to verify the provenance of cloud service software, for example, code
provided by a CSN. Where applicable, CSNs and their host CSPs provide a process to verify the
integrity of the CSN's software component to ensure that it is exactly as delivered and has not been
modified or compromised. Some CSNs may demand the means to verify this directly by themselves.
This capability is continuous to cover ongoing system evolution and updates.
10 Framework methodology
To develop a security framework for cloud computing means understanding what threats and challenges
exist, as was discussed in clauses 7 and 8, for the chosen specific cloud service along with the business,
technology and regulatory requirements which are to be taken together to identify security controls, policies
and procedures that will be needed for a given cloud service. The capabilities described in clause 9 to address
and mitigate these threats and challenges are then used to develop the security controls, policies and
procedures for the chosen specific cloud computing service. This Recommendation focuses on what the
needs are for security in a cloud computing environment, the threats and challenges of a traditional
computing environment exist within the cloud environment and as such following the standards and best
practices defined by the industry should be followed in addition to this Recommendation.
The methodology described here should be followed to create the framework that will identify what security
controls, policies and procedures will be needed for a specific given cloud computing service. It is not possible
to provide a single normative framework for all cloud computing services, since they vary greatly in business
model, services offered and implementation choices:
• Step 1: Use clauses 7 and 8 to identify security threats and security implications of the challenges in
the cloud computing service under study.
• Step 2: Use clause 9 to identify the needed high-level security capabilities based on identified threats
and challenges which could mitigate security threats and address security challenges.
• Step 3: Derive security controls, policies and procedures which could provide the security abilities
that are needed based on identified security capabilities.
NOTE – A set of appropriate requirements with respect to the security capabilities will need to be determined
by the CSC and CSP using appropriate standards. This determination will be based on the risk assessment.
To identify which security threats and challenges are relevant for the cloud service under study, each threat
or challenge should be reviewed. One approach could be as simple as a table showing a 'Y' next to the threat
or challenge.
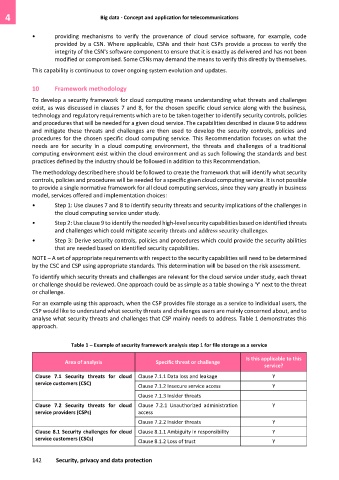
For an example using this approach, when the CSP provides file storage as a service to individual users, the
CSP would like to understand what security threats and challenges users are mainly concerned about, and to
analyse what security threats and challenges that CSP mainly needs to address. Table 1 demonstrates this
approach.
Table 1 – Example of security framework analysis step 1 for file storage as a service
Is this applicable to this
Area of analysis Specific threat or challenge
service?
Clause 7.1 Security threats for cloud Clause 7.1.1 Data loss and leakage Y
service customers (CSC)
Clause 7.1.2 Insecure service access Y
Clause 7.1.3 Insider threats
Clause 7.2 Security threats for cloud Clause 7.2.1 Unauthorized administration Y
service providers (CSPs) access
Clause 7.2.2 Insider threats Y
Clause 8.1 Security challenges for cloud Clause 8.1.1 Ambiguity in responsibility Y
service customers (CSCs)
Clause 8.1.2 Loss of trust Y
142 Security, privacy and data protection