Page 126 - Big data - Concept and application for telecommunications
P. 126
3 Big data - Concept and application for telecommunications
Table I.5 – Use case – Managing personal information
Title Managing personal information
Derived – Retrieve provenance information (see clause 8.1)
requirement – Verifying PII (see clause 8.4)
– Protecting PII (see clause 8.4)
– Sharing level for provenance (see clause 8.4)
– Simplifying provenance information (see clause 8.4)
Table I.6 – Use case – Reuse provenance information from the different analysis system
Title Reusing provenance information from the different analysis system
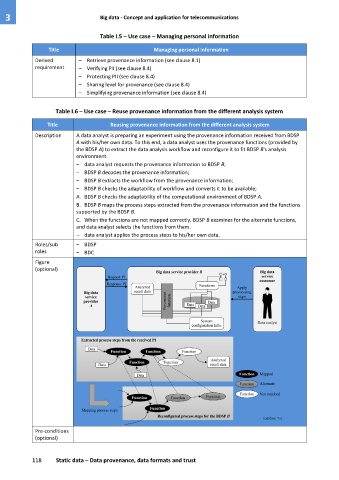
Description A data analyst is preparing an experiment using the provenance information received from BDSP
A with his/her own data. To this end, a data analyst uses the provenance functions (provided by
the BDSP A) to extract the data analysis workflow and reconfigure it to fit BDSP B's analysis
environment.
– data analyst requests the provenance information to BDSP B;
– BDSP B decodes the provenance information;
– BDSP B extracts the workflow from the provenance information;
– BDSP B checks the adaptability of workflow and converts it to be available;
A. BDSP B checks the adaptability of the computational environment of BDSP A.
B. BDSP B maps the process steps extracted from the provenance information and the functions
supported by the BDSP B.
C. When the functions are not mapped correctly, BDSP B examines for the alternate functions,
and data analyst selects the functions from them.
– data analyst applies the process steps to his/her own data.
Roles/sub – BDSP
roles – BDC
Figure
(optional)
Pre-conditions
(optional)
118 Static data – Data provenance, data formats and trust