Page 63 - Trust in ICT 2017
P. 63
Trust in ICT 1
Most importantly, the transition to the SCP infrastructure depends upon how to acquire useful knowledge
from data and information. Trust is essential in this knowledge acquisition process; also, for awareness and
understanding of a specific context it is really important to have confidence in decision making. In other
words, trust should be additionally considered in systems that behave intelligently and rationally to sense
real-world behaviour, perceive the world using information models, adapt to different environments and
changes, learn and build knowledge, and act to control their environments [47]. This is mainly related to the
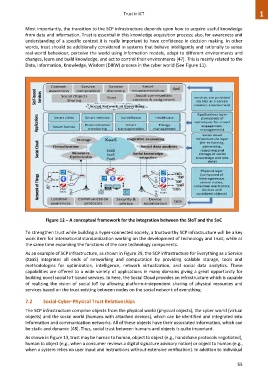
Data, Information, Knowledge, Wisdom (DIKW) process in the cyber world (See Figure 11).
Figure 12 – A conceptual framework for the integration between the SIoT and the SoC
To strengthen trust while building a hyper-connected society, a trustworthy SCP infrastructure will be a key
work item for international standardization working on the development of technology and trust, while at
the same time expanding the functions of the core technology components.
As an example of SCP infrastructure, as shown in Figure 29, the SCP infrastructure for Everything as a Service
(XaaS) integrates all ends of networking and computation by providing scalable storage, tools and
methodologies for optimization, intelligence, network virtualization, and social data analytics. These
capabilities are offered to a wide variety of applications in many domains giving a great opportunity for
building novel social IoT-based services. In here, the Social Cloud provides an infrastructure which is capable
of realizing the vision of social IoT by allowing platform-independent sharing of physical resources and
services based on the trust existing between nodes on the social network of everything.
7.2 Social-Cyber-Physical Trust Relationships
The SCP infrastructure comprise objects from the physical world (physical objects), the cyber world (virtual
objects) and the social world (humans with attached devices), which can be identified and integrated into
information and communication networks. All of these objects have their associated information, which can
be static and dynamic [48]. Thus, social trust between humans and objects is quite important.
As shown in Figure 13, trust may be human to human, object to object (e.g., handshake protocols negotiated),
human to object (e.g., when a consumer reviews a digital signature advisory notice) or object to human (e.g.,
when a system relies on user input and instructions without extensive verification). In addition to individual
55