Page 222 - Trust in ICT 2017
P. 222
3 Trust in ICT
5.4 Trust matrix
Trust matrix presents trust relationship among actors of this use case based on flow of data.
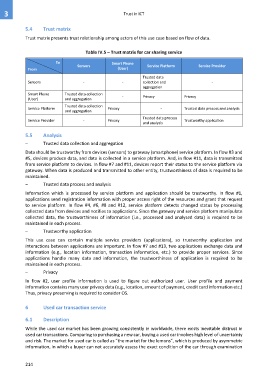
Table IV.5 – Trust matrix for car sharing service
To Smart Phone
Sensors Service Platform Service Provider
From (User)
Trusted data
Sensors - - collection and -
aggregation
Smart Phone Trusted data collection
(User) and aggregation - Privacy Privacy
Trusted data collection
Service Platform Privacy - Trusted data process and analysis
and aggregation
Trusted data process
Service Provider - Privacy Trustworthy application
and analysis
5.5 Analysis
– Trusted data collection and aggregation
Data should be trustworthy from devices (sensors) to gateway (smartphone) service platform. In flow #3 and
#5, devices produce data, and data is collected in a service platform. And, in flow #11, data is transmitted
from service platform to devices. In flow #7 and #11, devices report their status to the service platform via
gateway. When data is produced and transmitted to other entity, trustworthiness of data is required to be
maintained.
– Trusted data process and analysis
Information which is processed by service platform and application should be trustworthy. In flow #1,
applications send registration information with proper access right of the resources and grant that request
to service platform. In flow #4, #6, #8 and #12, service platform detects changed status by processing
collected data from devices and notifies to applications. Since the gateway and service platform manipulate
collected data, the trustworthiness of information (i.e., processed and analysed data) is required to be
maintained in each process.
– Trustworthy application
This use case can contain multiple service providers (applications), so trustworthy application and
interactions between applications are important. In flow #7 and #13, two applications exchange data and
information (e.g., location information, transaction information, etc.) to provide proper services. Since
applications handle many data and information, the trustworthiness of application is required to be
maintained in each process.
– Privacy
In flow #2, user profile information is used to figure out authorized user. User profile and payment
information contains many user privacy data (e.g., location, amount of payment, credit card information etc.)
Thus, privacy preserving is required to consider OS.
6 Used car transaction service
6.1 Description
While the used car market has been growing consistently in worldwide, there exists inevitable distrust in
used car transactions. Comparing to purchasing a new car, buying a used car involves high level of uncertainty
and risk. The market for used car is called as “the market for the lemons”, which is produced by asymmetric
information, in which a buyer can not accurately assess the exact condition of the car through examination
214