Page 63 - The Digital Financial Services (DFS) Ecosystem
P. 63
ITU-T Focus Group Digital Financial Services
Ecosystem
is getting to enroll at registration centers (Messmer, 2012). The e-KTP’s fingerprint verification system has a
false rejection rate of 3% or lower and a false acceptance rate of .01% or lower (Fahmi, 2012; Fauzi, 2014). In
addition, Uganda’s National Security Information System (NSIS) is supported with facial recognition technology
(FRS) and an Automatic Fingerprint Identification System (AFIS) to prevent identity forgery or loss (National
Security Information System, 2015b). In an address to the nation, Ugandan President Yoweri Musaveni specified
that NSIS also plans to capture citizens’ DNA to help combat crimes (State House Uganda, 2014).
We find evidence that programs in India, Nigeria, and Pakistan authenticate financial transactions on site
using biometric information. However, we find no evidence of countries having devices available for on-site
biometric verification during elections. This limited use of biometric verification is likely because biometric
authentication is costly, and may be less cost effective than traditional means of verification such as presenting a
physical ID (Gelb & Clark, 2013). As a result, while many programs include a central registry of citizen biometric
information, few possess the equipment to verify citizens on site for financial/social transfers, elections,
or other functions. Evidence of biometric authentication is discussed further in the sections on functional
applications of national ID programs.
Finally, several programs collect and digitise signatures, storing them on ID card electronic chips. Ten countries
incorporate this feature (Afghanistan, Iran, Bangladesh, Ecuador, Indonesia, Nigeria, Peru, Tanzania, Uganda,
and Ukraine). Castro writes that “digital signatures use a technique known as asymmetric cryptography
requiring two components: a private key for the sender to use to sign a document and a public key for
the receiver to use to verify the signature. The keys are generated by a certificate authority, a trusted third
party such as a private company or the government” (Castro, 2011, p. 4). For example, the Iranian National
Organization for Civil Registration states that for its new generation of ID cards an electronic signature will
enable document recipients to feel certain that what they receive is not counterfeit (Immigration and Refugee
Board of Canada, 2015). Digital signatures may facilitate online transactions by creating secure routes to send
financial, health, or other types of documents. However, we find no evidence in our literature review of the
extent to which digital signatures are used by citizens, nor examples of transactions in which digital signatures
are applied.
3.2 Stage of Implementation
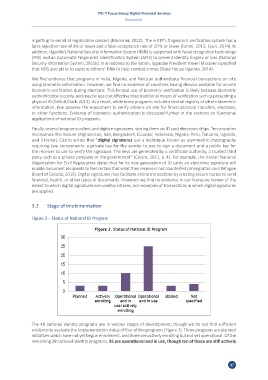
Figure 3 – Status of National ID Program
The 48 national identity programs are in various stages of development, though we do not find sufficient
evidence to evaluate the implementation status of four of the programs (Figure 3). Three programs are planned
initiatives which have not yet begun enrollment, and three are actively enrolling but not yet operational. Of the
remaining 38 national identity programs, 35 are operational and in use, though ten of these are still actively
47