Page 62 - The Digital Financial Services (DFS) Ecosystem
P. 62
ITU-T Focus Group Digital Financial Services
Ecosystem
More than half (28 of 48) of the programs we review include an electronic component in their physical
credentials. Many of programs use smartcards, where personal information and digital credentials are stored
securely on an embedded microchip. For example, the Second Generation Resident Identity Card in China
and the Carte Nationale D'Identite Electronique in Morocco both use a type of microchip that contains a
radio frequency identification (RFID) module (Immigration and Refugee Board of Canada, 2007; AGFA, 2015).
Other countries which specify the use of smartcards for their national identity program include Afghanistan,
Bangladesh, Ecuador, Egypt, Guatemala, Indonesia, Morocco, Nepal, Nigeria, Pakistan, Peru, Tanzania, Thailand,
and Ukraine. The use of smart chip technology creates a “platform to deploy applications needed by different
government [and private] sectors,” and is thus “an enabler of new services” (World Bank, 2014).
Machine-readable barcodes that record and protect personal and biometric information are another electronic
component of physical credentials used by a small number of countries (Congo, Ghana, Sri Lanka, Uganda, and
Zambia). For instance, the NSIS identity card in Uganda is a biometrically enhanced, machine readable card
with digitally embedded face scans and fingerprints of the card holder (National Security Information System
(NSIS, 2015b; Uganda Convention UK, 2014).
Name (30 programs), gender (25), and birth date (25) of the individual are the most common personal
information collected during registration. Other types of personal information collected include individuals’
signatures, ID number, place of birth, and religion. A photograph of the individual on the physical credential
is a feature in 38 of the programs reviewed.
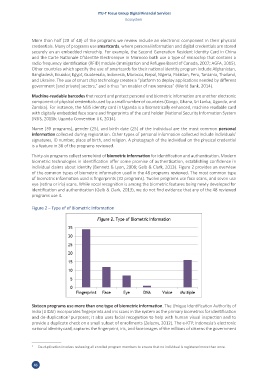
Thirty-six programs collect some kind of biometric information for identification and authentication. Modern
biometric technologies in identification offer some promise of authentication, establishing confidence in
individual claims about identity (Bennett & Lyon, 2008; Gelb & Clark, 2013). Figure 2 provides an overview
of the common types of biometric information used in the 48 programs reviewed. The most common type
of biometric information used is fingerprints (32 programs). Twelve programs use face scans, and seven use
eye (retina or iris) scans. While vocal recognition is among the biometric features being newly developed for
identification and authentication (Gelb & Clark, 2013), we do not find evidence that any of the 48 reviewed
programs use it.
Figure 2 – Type of of Biometric Information
Sixteen programs use more than one type of biometric information. The Unique Identification Authority of
India (UIDAI) incorporates fingerprints and iris scans in the system as the primary biometrics for identification
and de-duplication purposes; it also uses facial recognition to help with human visual inspection and to
3
provide a duplicate check on a small subset of enrollments (Zelazny, 2012). The e-KTP, Indonesia’s electronic
national identity card, captures the fingerprint, iris, and face images of the millions of citizens the government
3 De-duplication involves reviewing all enrolled program members to ensure that no individual is registered more than once.
46