Page 746 - Shaping smarter and more sustainable cities - Striving for sustainable development goals
P. 746
8.4 Infrastructure of Secondary Use of Data
72
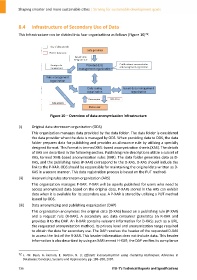
This infrastructure can be divided into four organizations as follows (Figure 10) .
Figure 10 – Overview of data anonymization infrastructure
(i) Original data storeroom organization (ODS)
This organization manages data provided by the data folder. The data folder is considered
the data provider when the data is managed by ODS. When providing data to ODS, the data
folder prepares data for publishing and provides an allowance rule by utilizing a specially
designed format. This format is termed XML‐based anonymization sheets (XAS). The details
of XAS are described in the following section. Publishing rule descriptions utilize a subset of
XAS, termed XML‐based anonymization rules (XAR). The data folder generates data as D‐
XAS, and the publishing rules (P‐XAR) correspond to the D‐XAS. D‐XAS should include the
link to the P‐XAR. ODS should be responsible for maintaining the original data written as D‐
XAS in a secure manner. This data registration process is based on the PUT method.
(ii) Anonymizing rules storeroom organization (ARS)
This organization manages P‐XAR. P‐XAR will be openly published for users who need to
access anonymized data based on the original data. P‐XARs stored in the ARS can exhibit
data when it is available for its secondary use. A P‐XAR is stored by utilizing a PUT method
issued by ODS.
(iii) Data anonymizing and publishing organization (DAP)
This organization anonymizes the original data (D‐XAS) based on a publishing rule (P‐XAR)
and a request rule (R‐XAR). A secondary use data consumer generates an R‐XAR and
provides it to the DAP. An R‐XAR contains relevant information for D‐XASs such as a URL,
the requested anonymization method, its privacy level and anonymization range required
to obtain the data for secondary use. The DAP receives the header of the requested D‐XAS
to access the link of the R‐XAR. This header information does not include data. This header
information is also described by using an XAR termed H‐XAR; the DAP verifies its compliance
____________________
72 J. ‐W. Byun, A. kamura, E. Bertino, N. Li; Efficient k‐anonymization using clustering techniques; Advances in
Databases: Concepts, Systems and Applications, pp. 188–200, 2007.
736 ITU‐T's Technical Reports and Specifications