Page 140 - Unleashing the potenti al of the Internet of Things
P. 140
3 Unleashing the potential of the Internet of Things
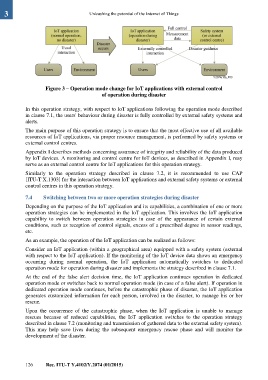
Figure 3 – Operation mode change for IoT applications with external control
of operation during disaster
In this operation strategy, with respect to IoT applications following the operation mode described
in clause 7.1, the users' behaviour during disaster is fully controlled by external safety systems and
alerts.
The main purpose of this operation strategy is to ensure that the most effective use of all available
resources of IoT applications, via proper resource management, is performed by safety systems or
external control centres.
Appendix I describes methods concerning assurance of integrity and reliability of the data produced
by IoT devices. A monitoring and control centre for IoT devices, as described in Appendix I, may
serve as an external control centre for IoT applications for this operation strategy.
Similarly to the operation strategy described in clause 7.2, it is recommended to use CAP
[ITU-T X.1303] for the interaction between IoT applications and external safety systems or external
control centres in this operation strategy.
7.4 Switching between two or more operation strategies during disaster
Depending on the purpose of the IoT application and its capabilities, a combination of one or more
operation strategies can be implemented in the IoT application. This involves the IoT application
capability to switch between operation strategies in case of the appearance of certain external
conditions, such as reception of control signals, excess of a prescribed degree in sensor readings,
etc.
As an example, the operation of the IoT application can be realized as follows:
Consider an IoT application (within a geographical area) equipped with a safety system (external
with respect to the IoT application). If the monitoring of the IoT device data shows an emergency
occurring during normal operation, the IoT application automatically switches to dedicated
operation mode for operation during disaster and implements the strategy described in clause 7.1.
At the end of the false alert decision time, the IoT application continues operation in dedicated
operation mode or switches back to normal operation mode (in case of a false alert). If operation in
dedicated operation mode continues, before the catastrophic phase of disaster, the IoT application
generates customized information for each person, involved in the disaster, to manage his or her
rescue.
Upon the occurrence of the catastrophic phase, when the IoT application is unable to manage
rescues because of reduced capabilities, the IoT application switches to the operation strategy
described in clause 7.2 (monitoring and transmission of gathered data to the external safety system).
This may help save lives during the subsequent emergency rescue phase and will monitor the
development of the disaster.
126 Rec. ITU-T Y.4102/Y.2074 (01/2015)