Page 60 - AI Ready – Analysis Towards a Standardized Readiness Framework
P. 60
AI Ready – Analysis Towards a Standardized Readiness Framework
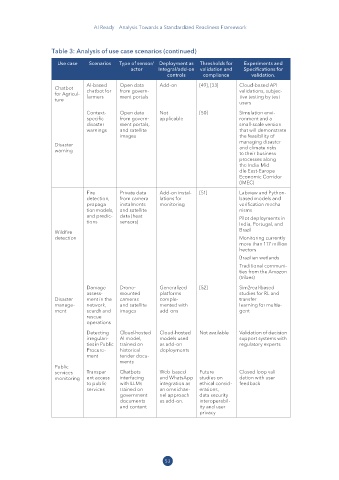
Table 3: Analysis of use case scenarios (continued)
Use case Scenarios Type of sensor/ Deployment as Thresholds for Experiments and
actor Integral/add-on validation and Specifications for
controls compliance validation�
AI-based Open data Add-on [49], [33] Cloud-based API
Chatbot chatbot for from govern- validations, subjec-
for Agricul- farmers ment portals tive testing by test
ture
users
Context- Open data Not [50] Simulation envi-
specific from govern- applicable ronment and a
disaster ment portals, small-scale version
warnings and satellite that will demonstrate
images the feasibility of
managing disaster
Disaster and climate risks
warning
to their business
processes along
the India-Mid-
dle East-Europe
Economic Corridor
(IMEC)
Fire Private data Add-on instal- [51] Labview and Python-
detection, from camera lations for based models and
propaga- instalments monitoring verification mecha-
tion models, and satellite nisms
and predic- data (heat Pilot deployments in
tions sensors) India, Portugal, and
Wildfire Brazil
detection Monitoring currently
more than 117 million
hectors
Brazilian wetlands
Traditional communi-
ties from the Amazon
(tribes)
Damage Drone- Generalized [52] Sim2real-based
assess- mounted platforms studies for RL and
Disaster ment in the cameras comple- transfer
manage- network, and satellite mented with learning for multia-
ment search and images add-ons gent
rescue
operations
Detecting Cloud-hosted Cloud-hosted Not available Validation of decision
irregulari- AI model, models used support systems with
ties in Public trained on as add-on regulatory experts
Procure- historical deployments
ment tender docu-
ments
Public
services Transpar- Chatbots Web-based Future Closed loop vali-
monitoring ent access interfacing and WhatsApp studies on dation with user
to public with LLMs integration as ethical consid- feedback
services trained on an omnichan- erations,
government nel approach data security
documents as add-on. interoperabil-
and content ity and user
privacy
53