Page 152 - Kaleidoscope Academic Conference Proceedings 2021
P. 152
2021 ITU Kaleidoscope Academic Conference
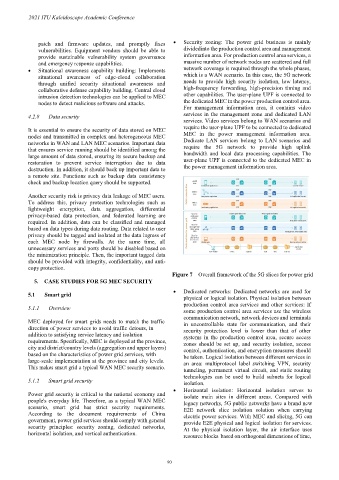
patch and firmware updates, and promptly fixes • Security zoning: The power grid business is mainly
vulnerabilities. Equipment vendors should be able to divided into the production control area and management
provide sustainable vulnerability system governance information area. For production control area services, a
and emergency response capabilities. massive number of network nodes are scattered and full
• Situational awareness capability building: Implements network coverage is required through the whole phases,
situational awareness of edge-cloud collaboration which is a WAN scenario. In this case, the 5G network
through unified security situational awareness and needs to provide high security isolation, low latency,
collaborative defense capability building. Central cloud high-frequency forwarding, high-precision timing and
intrusion detection technologies can be applied to MEC other capabilities. The user-plane UPF is connected to
nodes to detect malicious software and attacks. the dedicated MEC in the power production control area.
For management information area, it contains video
4.2.8 Data security services in the management zone and dedicated LAN
services. Video services belong to WAN scenarios and
It is essential to ensure the security of data stored on MEC require the user-plane UPF to be connected to dedicated
nodes and transmitted in complex and heterogeneous MEC MEC in the power management information area.
networks in WAN and LAN MEC scenarios. Important data Dedicate LAN services belong to LAN scenarios and
that ensures service running should be identified among the require the 5G network to provide high uplink
large amount of data stored, ensuring its secure backup and bandwidth and local data processing capabilities. The
restoration to prevent service interruption due to data user-plane UPF is connected to the dedicated MEC in
destruction. In addition, it should back up important data to the power management information area.
a remote site. Functions such as backup data consistency
check and backup location query should be supported.
Another security risk is privacy data leakage of MEC users.
To address this, privacy protection technologies such as
lightweight encryption, data aggregation, differential
privacy-based data protection, and federated learning are
required. In addition, data can be classified and managed
based on data types during data routing. Data related to user
privacy should be tagged and isolated at the data ingress of
each MEC node by firewalls. At the same time, all
unnecessary services and ports should be disabled based on
the minimization principle. Then, the important tagged data
should be provided with integrity, confidentiality, and anti-
copy protection.
Figure 7 – Overall framework of the 5G slices for power grid
5. CASE STUDIES FOR 5G MEC SECURITY
5.1 Smart grid • Dedicated networks: Dedicated networks are used for
physical or logical isolation. Physical isolation between
production control area services and other services: If
5.1.1 Overview some production control area services use the wireless
communication network, network devices and terminals
MEC deployed for smart grids needs to match the traffic in uncontrollable state for communication, and their
direction of power services to avoid traffic detours, in security protection level is lower than that of other
addition to satisfying service latency and isolation systems in the production control area, secure access
requirements. Specifically, MEC is deployed at the province, zones should be set up, and security isolation, access
city and district/country levels (aggregation and upper layers) control, authentication, and encryption measures should
based on the characteristics of power grid services, with be taken. Logical isolation between different services in
large-scale implementation at the province and city levels. an area: multiprotocol label switching VPN, security
This makes smart grid a typical WAN MEC security scenario. tunneling, permanent virtual circuit, and static routing
technologies can be used to build subnets for logical
5.1.2 Smart grid security isolation.
• Horizontal isolation: Horizontal isolation serves to
Power grid security is critical to the national economy and isolate main sites in different areas. Compared with
people's everyday life. Therefore, as a typical WAN MEC legacy networks, 5G public networks have a brand new
scenario, smart grid has strict security requirements. E2E network slice isolation solution when carrying
According to the document requirements of China electric power services. With MEC and slicing, 5G can
government, power grid services should comply with general provide E2E physical and logical isolation for services.
security principles: security zoning, dedicated networks, At the physical isolation layer, the air interface uses
horizontal isolation, and vertical authentication. resource blocks based on orthogonal dimensions of time,
– 90 –