Page 109 - ITU Journal Future and evolving technologies Volume 2 (2021), Issue 4 – AI and machine learning solutions in 5G and future networks
P. 109
ITU Journal on Future and Evolving Technologies, Volume 2 (2021), Issue 4
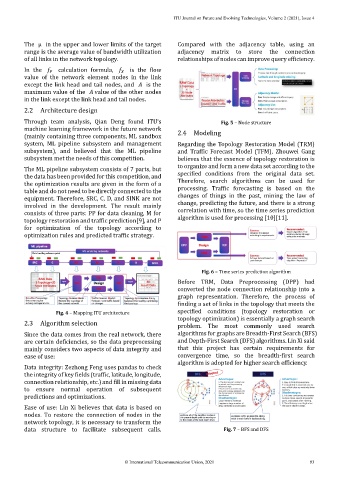
The μ in the upper and lower limits of the target Compared with the adjacency table, using an
range is the average value of bandwidth utilization adjacency matrix to store the connection
of all links in the network topology. relationships of nodes can improve query efficiency.
In the calculation formula, is the flow
value of the network element nodes in the link
except the link head and tail nodes, and is the
maximum value of the value of the other nodes
in the link except the link head and tail nodes.
2.2 Architecture design
Through team analysis, Qian Deng found ITU's Fig. 5 – Node structure
machine learning framework in the future network
(mainly containing three components, ML sandbox 2.4 Modeling
system, ML pipeline subsystem and management Regarding the Topology Restoration Model (TRM)
subsystem), and believed that the ML pipeline and Traffic Forecast Model (TFM), Zhouwei Gang
subsystem met the needs of this competition. believes that the essence of topology restoration is
to organize and form a new data set according to the
The ML pipeline subsystem consists of 7 parts, but
the data has been provided for this competition, and specified conditions from the original data set.
the optimization results are given in the form of a Therefore, search algorithms can be used for
table and do not need to be directly connected to the processing. Traffic forecasting is based on the
equipment. Therefore, SRC, C, D, and SINK are not changes of things in the past, mining the law of
involved in the development. The result mainly change, predicting the future, and there is a strong
consists of three parts: PP for data cleaning, M for correlation with time, so the time series prediction
topology restoration and traffic prediction[9], and P algorithm is used for processing [10][11].
for optimization of the topology according to
optimization rules and predicted traffic strategy.
Fig. 6 – Time series prediction algorithm
Before TRM, Data Preprocessing (DPP) had
converted the node connection relationship into a
graph representation. Therefore, the process of
finding a set of links in the topology that meets the
Fig. 4 – Mapping ITU architecture specified conditions (topology restoration or
topology optimization) is essentially a graph search
2.3 Algorithm selection problem. The most commonly used search
Since the data comes from the real network, there algorithms for graphs are Breadth-First Search (BFS)
are certain deficiencies, so the data preprocessing and Depth-First Search (DFS) algorithms. Lin Xi said
mainly considers two aspects of data integrity and that this project has certain requirements for
ease of use: convergence time, so the breadth-first search
algorithm is adopted for higher search efficiency.
Data integrity: Zezhong Feng uses pandas to check
the integrity of key fields (traffic, latitude, longitude,
connection relationship, etc.) and fill in missing data
to ensure normal operation of subsequent
predictions and optimizations.
Ease of use: Lin Xi believes that data is based on
nodes. To restore the connection of nodes in the
network topology, it is necessary to transform the
data structure to facilitate subsequent calls. Fig. 7 – BFS and DFS
© International Telecommunication Union, 2021 93