Page 55 - ITU Journal Future and evolving technologies Volume 2 (2021), Issue 1
P. 55
ITU Journal on Future and Evolving Technologies, Volume 2 (2021), Issue 1
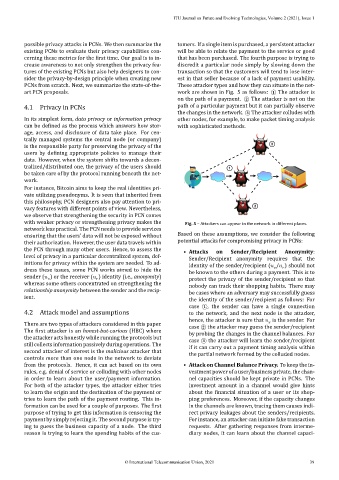
possible privacy attacks in PCNs. We then summarize the tomers. If a single item is purchased, a persistent attacker
existing PCNs to evaluate their privacy capabilities con‑ will be able to relate the payment to the service or good
cerning these metrics for the irst time. Our goal is to in‑ that has been purchased. The fourth purpose is trying to
crease awareness to not only strengthen the privacy fea‑ discredit a particular node simply by slowing down the
tures of the existing PCNs but also help designers to con‑ transaction so that the customers will tend to lose inter‑
sider the privacy‑by‑design principle when creating new est in that seller because of a lack of payment usability.
PCNs from scratch. Next, we summarize the state‑of‑the‑ These attacker types and how they can situate in the net‑
art PCN proposals. work are shown in Fig. 5 as follows: ⃝ The attacker is
1
on the path of a payment. ⃝ The attacker is not on the
2
4.1 Privacy in PCNs path of a particular payment but it can partially observe
the changes in the network. 3 ⃝ The attacker colludes with
In its simplest form, data privacy or information privacy other nodes, for example, to make packet timing analysis
can be de ined as the process which answers how stor‑ with sophisticated methods.
age, access, and disclosure of data take place. For cen‑
trally managed systems the central node (or company)
is the responsible party for preserving the privacy of the
users by de ining appropriate policies to manage their
data. However, when the system shifts towards a decen‑
tralized/distributed one, the privacy of the users should
be taken care of by the protocol running beneath the net‑
work.
For instance, Bitcoin aims to keep the real identities pri‑
vate utilizing pseudonyms. It is seen that inherited from
this philosophy, PCN designers also pay attention to pri‑
vacy features with different points of view. Nevertheless,
we observe that strengthening the security in PCN comes
with weaker privacy or strengthening privacy makes the Fig. 5 – Attackers can appear in the network in different places.
network less practical. The PCN needs to provide services
ensuring that the users’ data will not be exposed without Based on these assumptions, we consider the following
their authorization. However, the user data travels within potential attacks for compromising privacy in PCNs:
the PCN through many other users. Hence, to assess the • Attacks on Sender/Recipient Anonymity:
level of privacy in a particular decentralized system, def‑ Sender/Recipient anonymity requires that the
initions for privacy within the system are needed. To ad‑ identity of the sender/recipient ( / ) should not
dress these issues, some PCN works aimed to hide the be known to the others during a payment. This is to
sender ( ) or the receiver ( ) identity (i.e., anonymity) protect the privacy of the sender/recipient so that
whereas some others concentrated on strengthening the nobody can track their shopping habits. There may
relationship anonymity between the sender and the recip‑ be cases where an adversary may successfully guess
ient.
the identity of the sender/recipient as follows: For
case ⃝, the sender can have a single connection
1
4.2 Attack model and assumptions to the network, and the next node is the attacker,
hence, the attacker is sure that is the sender. For
There are two types of attackers considered in this paper. case 2 ⃝ the attacker may guess the sender/recipient
The irst attacker is an honest‑but‑curious (HBC) where by probing the changes in the channel balances. For
the attacker acts honestly while running the protocols but case 3 ⃝ the attacker will learn the sender/recipient
still collects information passively during operations. The if it can carry out a payment timing analysis within
second attacker of interest is the malicious attacker that the partial network formed by the colluded nodes.
controls more than one node in the network to deviate
from the protocols. Hence, it can act based on its own • Attack on Channel Balance Privacy. To keep the in‑
rules, e.g. denial of service or colluding with other nodes vestment power of a user/business private, the chan‑
in order to learn about the user/payment information. nel capacities should be kept private in PCNs. The
For both of the attacker types, the attacker either tries investment amount in a channel would give hints
to learn the origin and the destination of the payment or about the inancial situation of a user or its shop‑
tries to learn the path of the payment routing. This in‑ ping preferences. Moreover, if the capacity changes
formation can be used for a couple of purposes. The irst in the channels are known, tracing them causes indi‑
purpose of trying to get this information is censoring the rect privacy leakages about the senders/recipients.
payment by simply rejecting it. The second purpose is try‑ For instance, an attacker can initiate fake transaction
ing to guess the business capacity of a node. The third requests. After gathering responses from interme‑
reason is trying to learn the spending habits of the cus‑ diary nodes, it can learn about the channel capaci‑
© International Telecommunication Union, 2021 39