Page 24 - Cloud computing: From paradigm to operation
P. 24
1 Framework and requirements for cloud computing
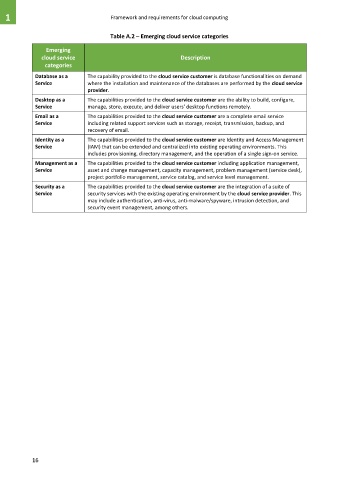
Table A.2 – Emerging cloud service categories
Emerging
cloud service Description
categories
Database as a The capability provided to the cloud service customer is database functionalities on demand
Service where the installation and maintenance of the databases are performed by the cloud service
provider.
Desktop as a The capabilities provided to the cloud service customer are the ability to build, configure,
Service manage, store, execute, and deliver users' desktop functions remotely.
Email as a The capabilities provided to the cloud service customer are a complete email service
Service including related support services such as storage, receipt, transmission, backup, and
recovery of email.
Identity as a The capabilities provided to the cloud service customer are Identity and Access Management
Service (IAM) that can be extended and centralized into existing operating environments. This
includes provisioning, directory management, and the operation of a single sign-on service.
Management as a The capabilities provided to the cloud service customer including application management,
Service asset and change management, capacity management, problem management (service desk),
project portfolio management, service catalog, and service level management.
Security as a The capabilities provided to the cloud service customer are the integration of a suite of
Service security services with the existing operating environment by the cloud service provider. This
may include authentication, anti-virus, anti-malware/spyware, intrusion detection, and
security event management, among others.
16