Page 1041 - Cloud computing: From paradigm to operation
P. 1041
Security 7
CSPs should also be transparent with CSCs when the patch is released on the cloud platform, and they should
communicate clearly with CSCs before patching. CSPs should try not to influence in any way CSC's services,
and this is through adopting appropriate measures together with CSCs.
4) Patch check
After the patches are released, CSPs should regularly check the patches with patch management tools to
make sure that the patches of the whole cloud platform are the latest. The document of patching records
should be updated regularly and should be archived for later security audits.
The waiting time between patch collect and update and CSCs approval requirement of patch update should
be explicit in the SLA, based on the priority type of the patch (e.g., critical, high, medium, and low).
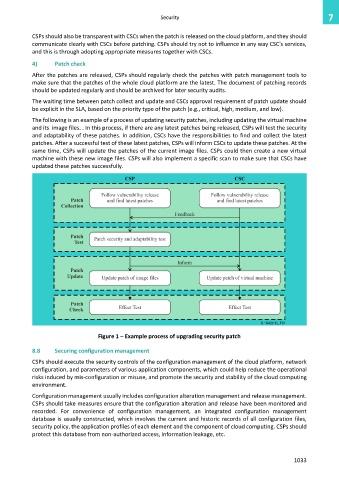
The following is an example of a process of updating security patches, including updating the virtual machine
and its image files. . In this process, if there are any latest patches being released, CSPs will test the security
and adaptability of these patches. In addition, CSCs have the responsibilities to find and collect the latest
patches. After a successful test of these latest patches, CSPs will inform CSCs to update these patches. At the
same time, CSPs will update the patches of the current image files. CSPs could then create a new virtual
machine with these new image files. CSPs will also implement a specific scan to make sure that CSCs have
updated these patches successfully.
Figure 1 – Example process of upgrading security patch
8.8 Securing configuration management
CSPs should execute the security controls of the configuration management of the cloud platform, network
configuration, and parameters of various application components, which could help reduce the operational
risks induced by mis-configuration or misuse, and promote the security and stability of the cloud computing
environment.
Configuration management usually includes configuration alteration management and release management.
CSPs should take measures ensure that the configuration alteration and release have been monitored and
recorded. For convenience of configuration management, an integrated configuration management
database is usually constructed, which involves the current and historic records of all configuration files,
security policy, the application profiles of each element and the component of cloud computing. CSPs should
protect this database from non-authorized access, information leakage, etc.
1033