Page 177 - ITU KALEIDOSCOPE, ATLANTA 2019
P. 177
ICT for Health: Networks, standards and innovation
knowledge, a spoken password that can be used to operate X.894 [11], can transfer encrypted content of any type or
PAKE. format using any symmetric encryption algorithm and a
named key. When this CMS type is used with BAKE or
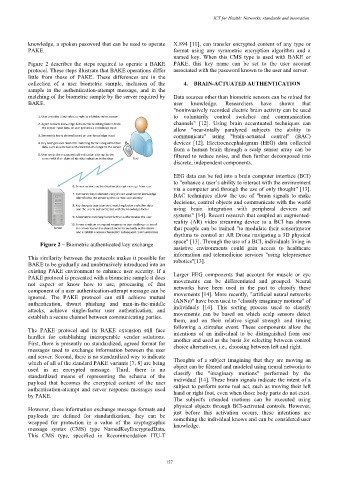
Figure 2 describes the steps required to operate a BAKE PAKE, this key name can be set to the user account
protocol. These steps illustrate that BAKE operations differ associated with the password known to the user and server.
little from those of PAKE. These differences are in the
collection of a user biometric sample, inclusion of the 4. BRAIN-ACTUATED AUTHENTICATION
sample in the authentication-attempt message, and in the
matching of the biometric sample by the server required by Data sources other than biometric sensors can be mined for
BAKE. user knowledge. Researchers have shown that
"noninvasively recorded electric brain activity can be used
to voluntarily control switches and communication
channels" [12]. Using brain accentuated techniques can
allow "near-totally paralyzed subjects the ability to
communicate" using "brain-actuated control" (BAC)
devices [12]. Electroencephalogram (EEG) data collected
from a human brain through a scalp sensor array can be
filtered to reduce noise, and then further decomposed into
discrete, independent components.
EEG data can be fed into a brain computer interface (BCI)
to "enhance a user’s ability to interact with the environment
via a computer and through the use of only thought" [13].
BAC techniques allow the use of "brain signals to make
decisions, control objects and communicate with the world
using brain integration with peripheral devices and
systems" [14]. Recent research that coupled an augmented-
reality (AR) video streaming device to a BCI has shown
that people can be trained "to modulate their sensorimotor
rhythms to control an AR Drone navigating a 3D physical
space" [13]. Through the use of a BCI, individuals living in
Figure 2 – Biometric authenticated key exchange
assistive environments could gain access to healthcare
information and telemedicine services "using telepresence
This similarity between the protocols makes it possible for robotics"[13].
BAKE to be gradually and unobtrusively introduced into an
existing PAKE environment to enhance user security. If a
PAKE protocol is presented with a biometric sample it does Larger EEG components that account for muscle or eye
movements can be differentiated and grouped. Neural
not expect or know how to use, processing of that
component of a user authentication-attempt message can be networks have been used in the past to classify these
movements [14]. More recently, "artificial neural networks
ignored. The PAKE protocol can still achieve mutual
authentication, thwart phishing and man-in-the-middle (ANNs)" have been used to "classify imaginary motions" of
individuals [14]. This sorting process used to classify
attacks, achieve single-factor user authentication, and
establish a secure channel between communicating parties. movements can be based on which scalp sensors detect
them, and on their relative signal strength and timing
following a stimulus event. These components allow the
The PAKE protocol and its BAKE extension still face intentions of an individual to be distinguished from one
hurdles for establishing interoperable vendor solutions. another and used as the basis for selecting between control
First, there is presently no standardized, agreed format for choice alternatives, i.e., choosing between left and right.
messages used to exchange information between the user
and server. Second, there is no standardized way to indicate
which of all of the standard PAKE variants [7, 8] are being Thoughts of a subject imagining that they are moving an
object can be filtered and modeled using neural networks to
used in an encrypted message. Third, there is no
standardized means of representing the schema of the classify the "imaginary motions" performed by the
individual [14]. These brain signals indicate the intent of a
payload that becomes the encrypted content of the user
authentication-attempt and server response messages used subject to perform some real act, such as moving their left
hand or right foot, even when those body parts do not exist.
by PAKE.
The subject's intended motions can be executed using
physical objects through BCI-activated controls. However,
However, these information exchange message formats and just before this activation occurs, these intentions are
payloads are defined for standardization, they can be something the individual knows and can be considered user
wrapped for protection in a value of the cryptographic knowledge.
message syntax (CMS) type NamedKeyEncryptedData.
This CMS type, specified in Recommendation ITU-T
– 157 –