Page 184 - Big data - Concept and application for telecommunications
P. 184
4 Big data - Concept and application for telecommunications
Appendix I
Guidelines for using security controls
(This appendix does not form an integral part of this Recommendation.)
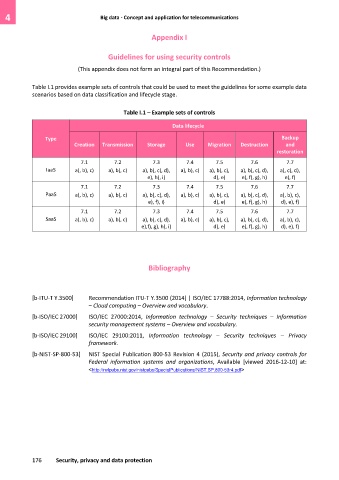
Table I.1 provides example sets of controls that could be used to meet the guidelines for some example data
scenarios based on data classification and lifecycle stage.
Table I.1 – Example sets of controls
Data lifecycle
Type Backup
Creation Transmission Storage Use Migration Destruction and
restoration
7.1 7.2 7.3 7.4 7.5 7.6 7.7
IaaS a), b), c) a), b), c) a), b), c), d), a), b), c) a), b), c), a), b), c), d), a), c), d),
e), h), i) d), e) e), f), g), h) e), f)
7.1 7.2 7.3 7.4 7.5 7.6 7.7
PaaS a), b), c) a), b), c) a), b), c), d), a), b), c) a), b), c), a), b), c), d), a), b), c),
e), f), i) d), e) e), f), g), h) d), e), f)
7.1 7.2 7.3 7.4 7.5 7.6 7.7
SaaS a), b), c) a), b), c) a), b), c), d), a), b), c) a), b), c), a), b), c), d), a), b), c),
e),f), g), h), i) d), e) e), f), g), h) d), e), f)
Bibliography
[b-ITU-T Y.3500] Recommendation ITU-T Y.3500 (2014) | ISO/IEC 17788:2014, Information technology
– Cloud computing – Overview and vocabulary.
[b-ISO/IEC 27000] ISO/IEC 27000:2014, Information technology – Security techniques – Information
security management systems – Overview and vocabulary.
[b-ISO/IEC 29100] ISO/IEC 29100:2011, Information technology – Security techniques – Privacy
framework.
[b-NIST-SP-800-53] NIST Special Publication 800-53 Revision 4 (2015), Security and privacy controls for
Federal information systems and organizations, Available [viewed 2016-12-10] at:
<http://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-53r4.pdf>
176 Security, privacy and data protection