Page 152 - First special issue on The impact of Artificial Intelligence on communication networks and services
P. 152
,78 -2851$/ ,&7 'LVFRYHULHV 9RO 0DUFK
7KURXJK RXU FRQWULEXWLRQ ZH DVSLUH WR HQULFK WKH GDWDVHW FRQVLVWHG RI WKH IROORZLQJ VHOHFWLRQ RI
YDULHW\ RI VFLHQWLILF PHWKRGV WKDW KDYH EHHQ HPSOR\HG F\EHUWKUHDW DOHUW SURWRFROV GHWHFWHG E\ WKH ,'6
VR IDU IRU WKH DQDO\VLV RI F\EHUDWWDFN SDWWHUQ UHFRJQLWLRQ
LQ FRPSXWHU QHWZRUNV¶ WUDIILF $V ZHOO DV WKH XVH RI
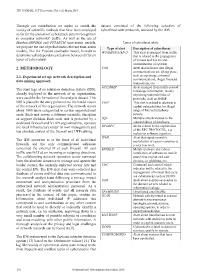
Markov,ARFIMA DQG FIGARCH WLPH VHULHV PRGHOV 7\SHV RI F\EHUWKUHDW DOHUWV
ZH SURSRVH WKH XVH RI SUREDELOLVWLF UHOHYDQW WLPH VHULHV Type of alert Description of cyberthreat
PRGHOV OLNH WKH Poisson VWRFKDVWLF PRGHO LQ RUGHU WR WORM/TROJAN () 7KLV DOHUW LV HPHUJHG IURP WUDIILF
GHWHUPLQH YDOLG GHSHQGHQFH UHODWLRQV EHWZHHQ GLIIHUHQW WKDW LV UHODWHG WR WKH SURSDJDWLRQ
W\SHV RI F\EHU DOHUWV RI YLUXVHV DQG ZRUPV DQG
FRQWDPLQDWLRQ RI V\VWHPV
2. METHODOLOGY TOR $OHUW WKDW LQGLFDWHV WKDW LOOHJDO
FRPPXQLFDWLRQV DUH WDNLQJ SODFH
2.1. Experiment set up: network description and VXFK DV HVSLRQDJH FULPLQDO
data mining approach FRPPXQLFDWLRQV LOOHJDO ILQDQFLDO
WUDQVDFWLRQV HWF
GPLSNMP $OHUW HPHUJHG IURP WUDIILF UHODWHG
7KH DOHUW ORJV RI DQ LQWUXVLRQ GHWHFWLRQ V\VWHP ,'6 WR OHDNDJH LQIRUPDWLRQ PDLQO\
DOUHDG\ GHSOR\HG LQ WKH QHWZRUN RI DQ RUJDQL]DWLRQ H[SORLWLQJ YXOQHUDELOLWLHV RI
ZHUH XVHG IRU WKH IRUPDWLRQ RI WKH DQDO\VLV GDWDVHW 7KLV SURWRFROV VXFK DV 6103
,'6 LV SODFHG LQ WKH HQWU\ SRLQW QH[W WR WKH ERUGHU URXWHU VOIP 7KLV DOHUW LV UHODWHG WR DWWHPSWV WR
RI WKH QHWZRUN RI WKH RUJDQL]DWLRQ 7KH QHWZRUN VHUYHV H[SORLW YXOQHUDELOLWLHV IRU LOOHJDO
DERXW XVHUV FDWHJRUL]HG LQ FHUWDLQ RUJDQL]DWLRQDO XVDJH RI ,QWHUQHW WHOHSKRQ\
XQLWV (DFK XQLW VHUYHV D GLIIHUHQW VFLHQWLILF GLVFLSOLQH VHUYHUV
RU VXSSRUW GLYLVLRQ (DFK VXFK XQLW LV SURWHFWHG E\ D SQL 0XOWLSOH DWWDFNV UHODWHG WR WKH
GHGLFDWHG ILUHZDOO DQG 9/$1 VHJPHQWDWLRQV RSHUDWHV YXOQHUDELOLWLHV RI GDWDEDVHV
WKH ORFDO LQIUDVWUXFWXUH XQGHU LWV RZQ PDQDJHPHQW DQG GPLRPC $OHUWV UHODWHG WR WKH H[SORLWDWLRQ
KDV DEVROXWH FRQWURO RI WKH ILUHZDOO DQG 873 FDEOLQJ RI WKH 53& 35272&2/ H J
PDOLFLRXV VRIWZDUH LQMHFWLRQ
IPMI $OHUW WKDW VLJQDOV SRVVLEOH
7KH ,'6 RSHUDWLRQ LV DW WKH IURQW RI DOO LQGLYLGXDO H[SORLWDWLRQ RI V\VWHP FRQVROHV DW
ILUHZDOOV DQG WKH RQO\ FRPPXQLFDWHG DGGUHVVHV D YHU\ ORZ OHYHO
FRQFHUQHG WKH H[WHUQDO ,3 RI HDFK ILUHZDOO $OO XVHU MOBILE 0RELOH PDOZDUH DOHUW DERXW
WUDIILF ZDV 1$7HG RQ LQFRPLQJ RU RXWJRLQJ GLUHFWLRQV LQVWDOODWLRQ RI VRIWZDUH WR PRELOH
7KH FROODERUDWLQJ QHWZRUN RSHUDWLRQ FHQWHU SHUVRQQHO VHDUFK WKDW H[SORLW HQG XVHU
KDYH WKH DEVROXWH FOHDUDQFH WR PDQDJH DQG RSHUDWH WKH GHYLFHV L H SKLVKLQJ HWF
ERUGHU URXWHUV WKH FHQWUDOO\ HQIRUFHG DFFHVV OLVWV DQG CNC &RPPDQG DQG FRQWURO ZKLFK
WKH FHQWUDO ,'6 7KH ,'6 DOHUW GDWD ZHUH FROOHFWHG LQ D LQGLFDWHV WUDIILF UHODWHG WR WKH
GDWDEDVH RI HYHQWV DQG WKDW GDWD ZDV FRPPXQLFDWHG WR PDQDJHPHQW RI ERWQHWV WKDW FDUU\
WKH UHVHDUFK DQDO\VW WHDP IROORZLQJ D SULYDF\ LPSDFW RXW F\EHUDWWDFNV VXFK DV ''26
DVVHVVPHQW DQG DQRQ\PL]DWLRQ SURFHGXUH IURP WKH DNS $OHUW DERXW VXVSLFLRXV TXHULHV WR
WKH GRPDLQ VHUYHUV UHODWHG WR
DXWKRUL]HG QHWZRUN DGPLQLVWUDWLRQ SHUVRQQHO $V D LQIRUPDWLRQ OHDNDJH
UHVXOW WKH GDWDEDVH RI HYHQWV DQG DOO UHVHDUFK GDWD SPAMHAUS 8QVROLFLWHG HPDLO WUDIILF
SURFHVVHG LQ WKH FRQWH[W RI WKLV SDSHU FRQWDLQ QR SCAN 1HWZRUN DFWLYLW\ UHODWHG WR H[WHUQDO
LQIRUPDWLRQ DERXW LQGLYLGXDO ,3 DGGUHVVHV WKDW DWWHPSWV WR UHFRQQDLVVDQFH
FRUUHVSRQG WR XVHU ZRUNVWDWLRQV RU DQ\ RWKHU FRQWHQW WRSRORJLHV QHWZRUN VHUYLFHV
WKDW FRXOG EH XVHG WR GLUHFWO\ RU LQGLUHFWO\ LGHQWLI\ D RSHUDWLQJ V\VWHPV LQ RUGHU WR
QHWZRUN XVHU L H E\ H[FOXVLRQ QDUURZLQJ GRZQ WR D H[SORLW YXOQHUDELOLWLHV
YHU\ VPDOO QXPEHU RI SRVVLEOH VXEMHFWV RU FRUUHODWLRQ MALWARE $OHUW DERXW WUDQVIRUPHG QRUPDO
DQG FURVV PDWFKLQJ ZLWK RWKHU SXEOLF LQIRUPDWLRQ $ VRIWZDUH ZLWK PDOLFLRXV SDUWV LQ
WKRURXJK DQDO\VLV RQ WKH SULYDF\ DQG OHJDO FKDOOHQJHV RUGHU WR H[SORLW XQDZDUH XVHUV
RI QHWZRUN UHVHDUFK FDQ EH IRXQG LQ > @ DDOS &\EHUDWWDFNV UHODWHG WR GHQLDO RI
COMPROMISED VHUYLFHV XQDEOH WR RSHUDWH
$OHUW DERXW V\VWHPV WKDW KDYH
7KH ,'6 V\VWHP XVHG LV WKH Suricata LQWUXGHU GHWHFWLRQ EHHQ SHQHWUDWHG
V\VWHP > @ EDVHG RQ WKH Oinkmaster UXOHVHW > @ 7KH
ORJ ILOH UHFRUGV RI F\EHUWKUHDW DOHUWV ZHUH UHODWHG WR WKH
PRVW IUHTXHQW DQG FRVWOLHVW W\SHV RI F\EHUDWWDFNV 2XU
,QWHUQDWLRQDO 7HOHFRPPXQLFDWLRQ 8QLRQ