Page 34 - Trust in ICT 2017
P. 34
1 Trust in ICT
Trust management
5.2.6 Document sharing
5.2.6.1 Description
This use case considers a social IoT environment [11] with no centralized trusted authority. In the social IoT,
each device has the subjective value between other devices based on the owner's social relationship as well
as the Community of Interest (CoI) [12] of each device.
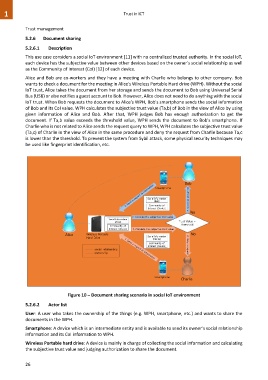
Alice and Bob are co-workers and they have a meeting with Charlie who belongs to other company. Bob
wants to check a document for the meeting in Alice's Wireless Portable Hard drive (WPH). Without the social
IoT trust, Alice takes the document from her storage and sends the document to Bob using Universal Serial
Bus (USB) or else notifies a guest account to Bob. However, Alice does not need to do anything with the social
IoT trust. When Bob requests the document to Alice's WPH, Bob's smartphone sends the social information
of Bob and its CoI value. WPH calculates the subjective trust value (Ta,b) of Bob in the view of Alice by using
given information of Alice and Bob. After that, WPH judges Bob has enough authorization to get the
document. If Ta,b value exceeds the threshold value, WPH sends the document to Bob's smartphone. If
Charlie who is not related to Alice sends the request query to WPH, WPH calculates the subjective trust value
(Ta,c) of Charlie in the view of Alice in the same procedure and deny the request from Charlie because Ta,c
is lower than the threshold. To prevent the system from Sybil attack, some physical security techniques may
be used like fingerprint identification, etc.
Figure 10 – Document sharing scenario in social IoT environment
5.2.6.2 Actor list
User: A user who takes the ownership of the things (e.g. WPH, smartphone, etc.) and wants to share the
documents in the WPH.
Smartphone: A device which is an intermediate entity and is available to send its owner’s social relationship
information and its CoI information to WPH.
Wireless Portable hard drive: A device is mainly in charge of collecting the social information and calculating
the subjective trust value and judging authorization to share the document.
26