Page 409 - Unleashing the potenti al of the Internet of Things
P. 409
Unleashing the potential of the Internet of Things 4
In order to provide verification applications, verification networks are used. A verification network
consists of devices and communication channels which are used to fetch and process the above
described values. A verification network can have some elements which are also SCN objects or
that constitute a part of the SCN infrastructure. A verification network may have much more strict
requirements concerning reliability, security and performance compared to other SCN applications.
Data processing and transmission for the purpose of verification may have higher priority in QoS in
comparison with other operations of SCN applications.
Examples of operations which require verification, verification rules and verification network
elements are given below.
The operations in a verification network can be executed once before critical operations of SCN
applications, or at the time of these operations or periodically. For each possible machine actuator
state and detected verification rule failure, some operations should be defined to be performed
instead of those given by the SCN application when one of the verification rules is mismatched.
Such operations can be, for example:
– Immediate machine actuator stop.
– State transition of the machine actuator to some safe state.
– Alarm notification to authorized personnel administrating the SCN.
– Generation of a log entry.
– No action.
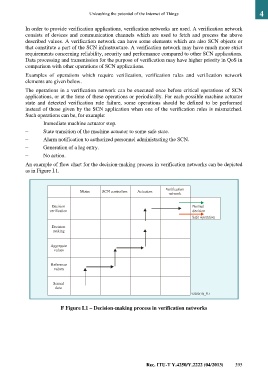
An example of flow chart for the decision-making process in verification networks can be depicted
as in Figure I.1.
Verification
Motes SCN controllers Actuators network
Decision Normal
verification decision
Safe operation
Decision
making
Aggregate
values
Reference
values
Sensed
data
Y.2222(13)_FI.1
F Figure I.1 – Decision-making process in verification networks
Rec. ITU-T Y.4250/Y.2222 (04/2013) 395