Page 134 - ITU Kaleidoscope 2016
P. 134
2016 ITU Kaleidoscope Academic Conference
ing resource management. In particular this last point is
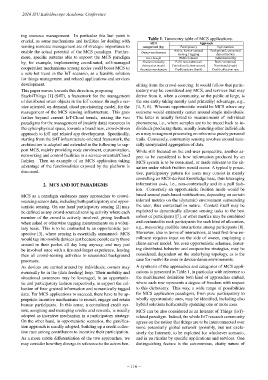
Table 1. Taxonomy table of MCS applications.
crucial, as some mechanisms and facilities for dealing with
MCS Approach
sensing resource management are of strategic importance to categorized (by) Participatory Opportunistic
enable the actual potential of the MCS paradigm. Further- Owner involvement Active, human-assisted Background, unmanned
sensing / tagging data collection
more, specific patterns able to support the MCS paradigm User benefit Public interest Individual utility
by, for example, implementing coordinated, self-managed Fruition modality Pull / non-contextual Push / contextual
Interaction model Centralized (client-server) Distributed (mesh)
cooperation mechanisms among nodes could boost MCS to Incentive mechanism Credit systems (bank) Credit collection race
a new-hot trend in the IoT scenario, as a feasible solution
for things management and related applications and services
development. efiting from the crowd-sourcing. It would follow that partic-
This paper moves towards this direction, proposing ipatory may be considered any MCS, and services that may
Stack4Things [1] (S4T), a framework for the management derive from it, when a community, or the public at large, is
of distributed smart objects in the IoT context through a ser- the one entity taking mostly (and primarily) advantage, e.g.,
vice oriented, on-demand, cloud provisioning model, for the [4, 5, 6]. Whereas opportunistic would be MCS where any
management of the MCS sensing infrastructure. This goes outcome would eminently center around single individuals.
further beyond current IoT-Cloud trends, mixing the two The latter is usually linked to measurements of individual
paradigms for the management of (mainly data) resources in phenomena, i.e., where samples are to be traced back to in-
the cyber-physical space, towards a brand new, crowd-driven dividuals producing them, usually featuring other individuals
approach to IoT and related app development. Specifically, as a way to augment processing on otherwise purely personal
starting from the S4T infrastructure-oriented framework, the trails. Conversely, community sensing revolves around natu-
architecture is adapted and extended in the following to sup- rally anonymized aggregation of data.
port MCS, mainly providing node enrolment, customization, While still focused on the end-user perspective, another as-
networking and control facilities in a service-oriented/Cloud pect to be considered is how information produced by an
fashion. Then an example of an MCS application taking MCS system is to be consumed, or made relevant to the sit-
advantage of the functionalities exposed by the platform is uation under which fruition would occur. A typically proac-
discussed. tive, participatory pattern for users may consist in merely
consulting an MCS-derived knowledge base, thus leveraging
2. MCS AND IOT PARADIGMS information as-is, i.e., non-contextually and in a pull fash-
ion. Conversely an opportunistic fruition mode would be
MCS as a paradigm embraces many approaches to crowd- based around push-based notifications, depending on certain
sourcing sensor data, including both participatory and oppor- inferred metrics on the (dynamic) environment surrounding
tunistic sensing. On one hand participatory sensing [2] may the user, thus contextual in nature. Context itself may be
be defined as any crowd-sourced sensing activity where each exploited to dynamically allocate sensing tasks to the best
member of the crowd is actively involved, giving feedback subset of participants [7], or other metrics may be combined
when asked or otherwise tagging measurements on a volun- and evaluated to rank participants for such kind of allocation,
tary basis. This is to be contrasted to an opportunistic per- e.g., measuring credible interactions among participants [8].
spective [3], where sensing is essentially unmanned: MCS Moreover, also in terms of interactions, at least first-time en-
would tap into mobile devices just because people carry those rollment requires input on the side of owner, employing a
around in their pocket all day long anyway, and may just client-server model. Yet even opportunistic schemes, featur-
be involved once with a fire-and-forget experience, leaving ing distributed behavior and cooperative strategies, may be
then all crowd-sensing activities to unassisted background considered, dependent on the underlying topology, as is the
processes. case for mesh-like ones in device-dense environments.
As devices are carried around by individuals, owners may A synthesis of the approaches and categories of MCS appli-
eventually be in the (data feeding) loop. Their mobility and cations is presented in Table 1, in particular with reference to
situational awareness may be leveraged, in an opportunis- the multifaceted definition both kind of approaches embed,
tic and participatory fashion respectively, to support the col- where each row represents a degree of freedom with respect
lection of finer grained information and semantically tagged to this dichotomy. This way, a wide range of possibilities
data. For MCS applications to succeed, there have to be ap- for MCS application paradigms, from pure participatory to
propriate incentive mechanisms to recruit, engage and retain wholly opportunistic ones, may be identified, including also
human participants. In this sense, a centralized credit sys- hybrid solutions horizontally spanning one or more axes.
tem, assigning and managing credits and rewards, is usually MCS can be also considered as an Internet of Things (IoT)-
adopted as incentive mechanism in a participatory strategy. related paradigm. Indeed, the whole IoT research community
On the other hand, in opportunistic scenarios, the gamifica- agrees on the notion that things are to be interconnected over
tion approach is usually adopted, building up a credit collec- some potentially global network (possibly, but not exclu-
tion race among contributors to incentive their participation. sively the Internet), to be exploited for whichever scenario,
As a more subtle differentiation of the two approaches, we and in pa rticular by specific applications and services. One
may consider how they diverge in reference to the actors ben- distinguishing feature is the autonomous, chatty nature of
– 116 –