Creating trust in critical network
infrastructures
Danger can come from almost anywhere…
Chain reaction
The potential extent of damage is
illustrated by a recent incident in which a handful of optical cables
located in a European country’s harbour were cut. This not only disabled the
Internet, but it also resulted in the partial loss of that country’s mobile
and fixed telephone services, emergency numbers, fax and data traffic, as well
as financial and PIN (personal identification number) code services. With so
many major services at risk, it is easy to understand why everyone should feel
concerned.
|
Network predators, disgruntled employees, corporate spies, electronic criminals, cyberterrorists, hostile
nations... Threats to the world’s communication networks come in many guises.
Yet, as infocommunications increasingly become the underpinning of our global
economy and society, we are ever more dependent upon these very networks. The
security of our global networks is a pressing issue that merits constant
attention — ensuring our collective cyber-security needs to be a top policy
priority.
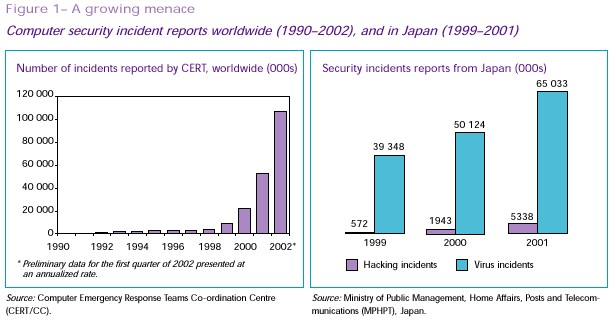
By all accounts, the threats to our networks are growing, and
the financial impact alone is alarmingly high. Almost every country that
collects statistics on security incidents has reported the growing scale of the
problem. Data compiled by the Computer Emergency Response Teams Coordination
Centre (CERT/CC) based at Carnegie Mellon University in the United States shows,
for example, that more security incidents (52 658) were reported in 2001 alone
than for the entire period since 1988, when records began. And the trend seems
to be continuing: preliminary statistics for the first quarter of 2002 show that
the rate of growth is still accelerating (see Figure 1, left chart). Japanese
Government statistics show that the number of virus incidents almost doubled,
and hacking incidents increased tenfold, between 1999 and 2001 (see Figure 1,
right chart). The cost of cyber-security breaches is currently estimated at
hundreds of billions of dollars annually.
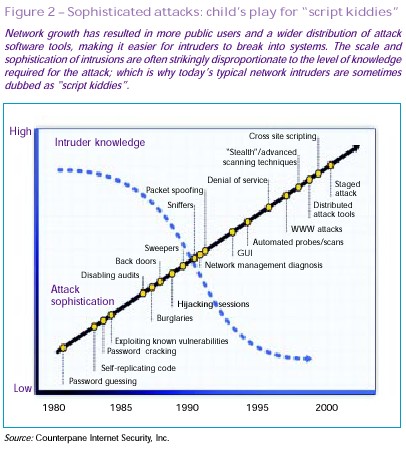
More networks, greater vulnerability
After over 100 years of development,
even the global telephone network is not entirely secure. But the telephone
network security still compares well with that of the Internet, which has even
greater shortcomings. With today’s rapid convergence of voice and data
networks, security issues need to be addressed in a context which covers the
global telephone network, wireless and satellite networks, the Internet, and the
many private networks used for critical services such as banking and health
care. Measures should also include a full assessment of physical infrastructure,
both hardware and software, as these form an integral part of any effective
solution.
An ITU Strategic Planning Workshop entitled “Creating Trust
in Critical Network Infrastructures” was held in Seoul (Republic of Korea)
from 20 to 22 May 2002*. A recurring theme in the workshop presentations and
discussions was the need for international collaboration for the protection of
critical network infrastructures. The workshop served to highlight the
inadequacy of current levels of collaboration. Moreover, activity at the
national level is insufficient and patchy in almost all countries. It was
concluded that critical infrastructure protection is urgently needed at three
levels: international, national, and sub-national.
 As well as identifying the status, needs and priorities of
network security, the workshop also discussed the form that international
collaboration might take. As an example, in his paper to the workshop,
Professor Goodman sets out a fivefold framework for international collaboration
involving: As well as identifying the status, needs and priorities of
network security, the workshop also discussed the form that international
collaboration might take. As an example, in his paper to the workshop,
Professor Goodman sets out a fivefold framework for international collaboration
involving:
-
International standards.
International cooperation in developing standards is increasingly
important, even in competitive markets. But equally important is cooperation
in the creation and implementation of standards. For instance, the IEEE
802.11 Wireless LAN security standard (WEP) is successfully implemented on
fewer than 15 per cent of Wireless LANs in operation, and it is relatively
easy to break.
-
Information sharing.
There is an understandable unwillingness to share information about
cyberattacks, if only for fear of exposing failings and undermining
public confidence. There may be a role for a clearinghouse function
— a role that an international organization could play, as a trusted
repository of up-to-date information. Such a clearinghouse could provide
anonymity to the victims as well as coordinating information gathering and
dissemination.
-
Halting cyberattacks in progress. One
of the most useful steps would be to develop a standard methodology
for the sharing of information across borders, especially during
cyberattacks, when time is of the essence. Stephen Bryen, in his paper,
proposed the creation of a “cyber-warning centre”, which could set
common data reporting standards and could serve as an alert service. This
could be combined with the clearinghouse function mentioned above.
-
Coordinating legal systems.
If defence against criminal or terrorist activities is to be active, rather
than passive, then there needs to be some coordination of legal systems so
that hackers cannot find safe havens.
-
Providing assistance to developing
nations. This will require collaboration between
ITU Member States at different levels of economic and technological
development. For example, the International Civil Aviation Organization
(ICAO) has played a similar role in providing technical assistance to
promote safety and security in civil aviation. Similar assistance is
necessary to counter cybercrime.

|
National and international responsibilities in the
face of a global problem
Nowadays, networks are typically
operated and managed by the private sector. Nevertheless, responsibility
for our personal security, social well-being and protection of life
clearly lies with national governments. Where appropriate, governments, in
consultation with the relevant industry sectors, need to begin a process of risk
assessment of the vulnerabilities and risks to national networks, with a view to
producing a follow-up action plan. In addition, existing mechanisms, activities,
and institutions already at work on aspects of critical infrastructure
protection need to be identified with a view to future coordination and
collaboration without duplication of efforts.
That said, national efforts will clearly not be enough: today’s
international networks do not recognize national boundaries, making this a
global problem requiring global action. Uncoordinated measures taken by
individual industry sectors or governments in isolation are likely to fail.
Governments, regulators, industry, hardware manufacturers, software developers
and users will all need to work together to assure our collective cybersecurity.
In this regard, the Chairman’s Report of the workshop suggested a number of
possible action areas for ITU. This included a suggestion that ITU quickly
review its current work programme vis-à-vis information systems security
and network infrastructure protection, and that it take action to reinforce its
activities accordingly. It was considered that ITU, as an organization with
across-the-board representation from governments and the private sector, and
with responsibility for coordinating global telecommunication networks and
services, including IP-based networks, provided a potential valuable
international forum for cooperation in this area.
|

 As well as identifying the status, needs and priorities of
network security, the workshop also discussed the form that international
collaboration might take. As an example, in his paper to the workshop,
Professor Goodman sets out a fivefold framework for international collaboration
involving:
As well as identifying the status, needs and priorities of
network security, the workshop also discussed the form that international
collaboration might take. As an example, in his paper to the workshop,
Professor Goodman sets out a fivefold framework for international collaboration
involving: